by Liquid Video Technologies | Mar 15, 2021 | Cybersecurity, Data Breaches, Network Security, Security, Security Breach
Researchers have discovered a new side-channel that they say can be reliably exploited to leak information and tracking users from web browsers that could then be leveraged to track users even when JavaScript is completely disabled. “This is a side-channel...
by Liquid Video Technologies | Mar 12, 2021 | Cybersecurity, Data Breaches, Security, Security Breach
Cybercriminals are now deploying remote access Trojans (ObliqueRAT) under the guise of seemingly innocuous images hosted on infected websites, once again highlighting how threat actors quickly change tactics when their attack methods are discovered and exposed...

by Liquid Video Technologies | Mar 10, 2021 | Cybersecurity, Data Breaches, Network Security, Security, Security Breach
Microsoft has released emergency patches to address four previously undisclosed security flaws in Exchange Server that it says are being actively exploited by a new Chinese state-sponsored threat actor with the goal of perpetrating data theft. Describing the attacks...

by Liquid Video Technologies | Mar 8, 2021 | Cybersecurity, Data Breaches, Security Breach, Technology News
Exactly a month after patching an actively exploited zero-day flaw in Chrome, Google today rolled out fixes for yet another zero-day vulnerability in the world’s most popular web browser that it says is being abused in the wild. Chrome 89.0.4389.72, released by...
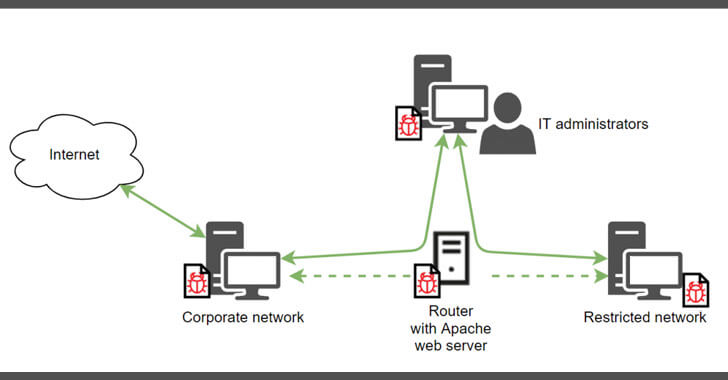
by Liquid Video Technologies | Mar 5, 2021 | Cybersecurity, Data Breaches, Network Security, Security, Security Breach
A prolific North Korean state-sponsored hacking group has been tied to a new ongoing espionage campaign aimed at exfiltrating sensitive information from organizations in the defense industry through ThreatNeedle malware. Attributing the attacks with high confidence to...
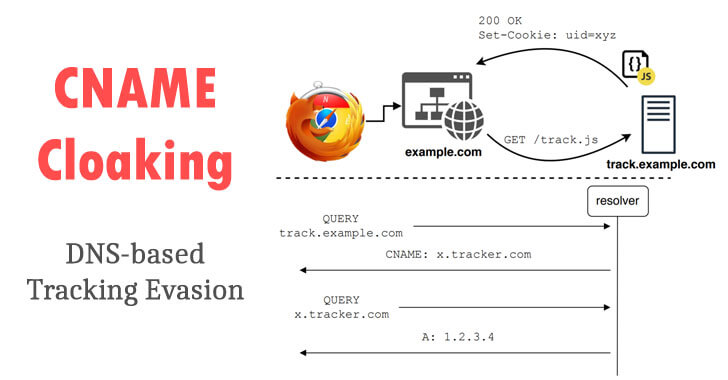
by Liquid Video Technologies | Mar 3, 2021 | Cybersecurity, Data Breaches, Network Security, Security, Security Breach
Called CNAME Cloaking, the practice of blurring the distinction between first-party and third-party cookies not only results in leaking sensitive private information without users’ knowledge and consent but also “increases [the] web security threat...
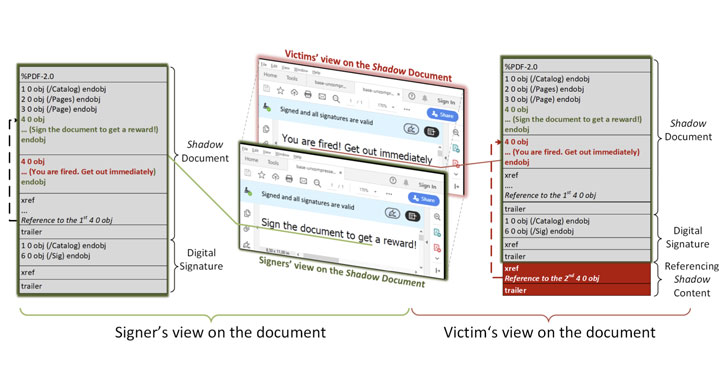
by Liquid Video Technologies | Mar 1, 2021 | Cybersecurity, Data Breaches, Security, Security Breach
Called “Shadow attacks” by academics from Ruhr-University Bochum, the technique uses the “enormous flexibility provided by the PDF specification so that shadow documents remain standard-compliant.” The findings were presented yesterday at the...
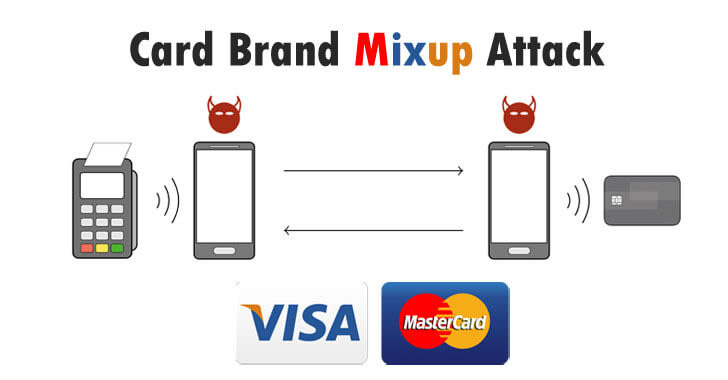
by Liquid Video Technologies | Feb 26, 2021 | Cybersecurity, Data Breaches, Security Breach
Cybersecurity researchers have disclosed a novel attack that could allow criminals to trick a point of sale terminal into transacting with a victim’s Mastercard contactless card while believing it to be a Visa card. The research, published by a group of...

by Liquid Video Technologies | Feb 24, 2021 | Cybersecurity, Data Breaches, Technology News
Microsoft on Thursday said it concluded its probe into the SolarWinds hack, finding that the attackers stole some source code but confirmed there’s no evidence that they abused its internal systems to target other companies or gained access to production...
by Liquid Video Technologies | Feb 22, 2021 | Cybersecurity, Data Breaches
Russia-linked state-sponsored threat actor known as Sandworm has been linked to a three-year-long stealthy operation to hack targets by exploiting an IT monitoring tool called Centreon. The intrusion campaign — which breached “several French entities” — is...









Recent Comments