Called “Shadow attacks” by academics from Ruhr-University Bochum, the technique uses the “enormous flexibility provided by the PDF specification so that shadow documents remain standard-compliant.”
The findings were presented yesterday at the Network and Distributed System Security Symposium (NDSS), with 16 of the 29 PDF viewers tested — including Adobe Acrobat, Foxit Reader, Perfect PDF, and Okular — found vulnerable to shadow attacks.
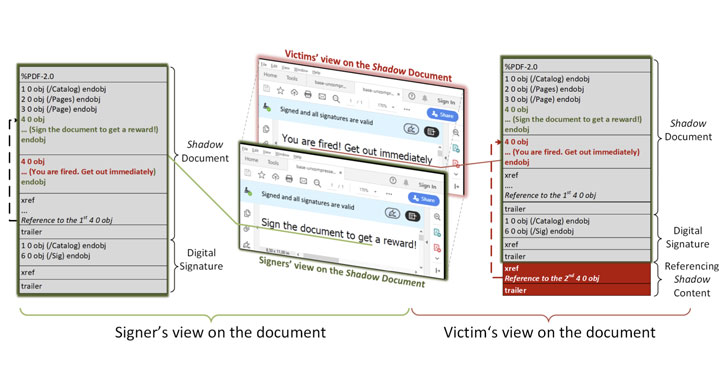
To carry out the attack, a malicious actor creates a PDF document with two different contents: one which is the content that’s expected by the party signing the document, and the other, a piece of hidden content that gets displayed once the PDF is signed.
“The signers of the PDF receive the document, review it, and sign it,” the researchers outlined. “The attackers use the signed document, modify it slightly, and send it to the victims. After opening the signed PDF, the victims check whether the digital signature was successfully verified. However, the victims see different content than the signers.”
In the analog world, the attack is equivalent to deliberately leaving empty spaces in a paper document and getting it signed by the concerned party, ultimately allowing the counterparty to insert arbitrary content in the spaces.
Shadow attacks build upon a similar threat devised by the researchers in February 2019, which found that it was possible to alter an existing signed document without invalidating its signature, thereby making it possible to forge a PDF document.
At its core, the attacks leverage “harmless” PDF features which do not invalidate the signature, such as “incremental update” that allows for making changes to a PDF (e.g., filling out a form) and “interactive forms” (e.g., text fields, radio buttons, etc.) to hide the malicious content behind seemingly innocuous overlay objects or directly replace the original content after it’s signed.
A third variant called “hide and replace” can be used to combine the aforementioned methods and modify the contents of an entire document by simply changing the object references in the PDF.
“The attacker can build a complete shadow document influencing the presentation of each page, or even the total number of pages, as well as each object contained therein,” the researchers said.
Put simply, the idea is to create a form, which shows the same value before and after signing, but a completely different set of values post an attacker’s manipulation.
To test the attacks, the researchers have published two new open-source tools called PDF-Attacker and PDF-Detector that can be used to generate shadow documents and test a PDF for manipulation before it’s signed and after it’s been altered.
The flaws — tracked as CVE-2020-9592 and CVE-2020-9596 — have been since addressed by Adobe in an update released on May 12, 2020. As of December 17, 2020, 11 of the 29 tested PDF applications remain unpatched.
This is not the first time PDF security has come under the lens. The researchers have previously demonstrated methods to extract contents of a password-protected PDF file by taking advantage of partial encryption supported natively by the PDF specification to remotely exfiltrate content once a user opens that document.
Separately, the researchers last month uncovered another set of 11 vulnerabilities impacting the PDF standard (CVE-2020-28352 through CVE-2020-28359, and from CVE-2020-28410 to CVE-2020-28412) that could lead to denial-of-service, information disclosure, data manipulation attacks, and even arbitrary code execution.
Article Provided By: The Hacker News
![]()
If you would like liquidvideotechnologies.com to discuss developing your Home Security System, Networking, Access Control, Fire, IT consultant, or PCI Compliance, please do not hesitate to call us at 864-859-9848 or you can email us at deveren@liquidvideotechnologies.com.

Recent Comments