by LVT_Admin | Jun 27, 2022 | Computer Networking
Ever found yourself needing to know how IP addressing works? How do we connect multiple computers by Ethernet cables? What is a network switch and why do I need one? Do you have any questions about the basics of computer networking, then this blog post is for you!...

by LVT_Admin | Jun 3, 2022 | Computer Networking
Computer networking is a buzzword to the present world. By the virtue of computer networking, the world has become just like a village. So, anyone in the world can communicate with any person of the world within seconds as if they are living in a village. Computer...

by LVT_Admin | May 27, 2022 | Computer Networking
The Internet is the world’s largest computer network. Let’s break that down A computer network is any group of interconnected computing devices capable of sending or receiving data. A computing device isn’t just a computer—it’s any device that...
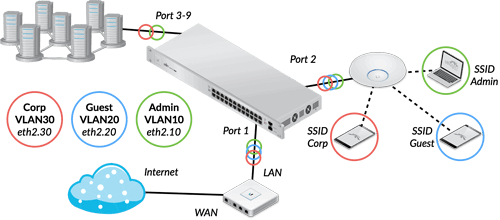
by LVT_Admin | May 6, 2022 | Computer Networking
Information is the building block for effective communication. Communication is the universal currency that knits us together and drives our day-to-day operations. Computer networking is a favorite among many businesses. You’re probably thinking about how important is...

by LVT_Admin | Mar 28, 2022 | Computer Networking
Computer networking is a major discipline that covers the different technologies, such as computer hardware and protocols, needed to connect computers as well as the operating systems and software used on those computers. It’s not just about connecting computers...

by LVT_Admin | Feb 18, 2022 | Computer Networking, Network Security, Technology, Technology News
Computer network technology continues to develop in new and interesting ways. Here are five of the most important areas and trends to watch in the year ahead. IoT Gadgets Will Become Commonplace In 2022, an array of internet-connected products will compete for...








Recent Comments