Networking News
Liquid Video Technologies, Inc. is here to help you. Not understanding the services we provide or need more information on other matters? These blog posts are here to help you and keep you up-to-date.
Mirai Variant and ZHtrap Botnet Malware
Cybersecurity researchers on Monday disclosed a new wave of ongoing attacks exploiting multiple vulnerabilities to deploy new Mirai variants on internet-connected devices. "Upon successful exploitation, the attackers try to download a malicious shell script, which...
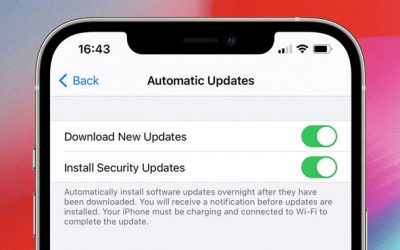
Apple Delivering Security Patches Separately
Apple may be changing the way it delivers security patches to its devices running iOS and iPadOS mobile operating systems. According to code spotted in iOS 14.5, the iPhone maker is reportedly working on a method for delivering security fixes independently of other OS...
Android Apps Disturbing MRAT Malware
Cybersecurity researchers have discovered a new malware dropper contained in as many as 9 Android apps distributed via Google Play Store that deploys a second stage malware capable of gaining intrusive access to the financial accounts of victims as well as full...
Linux Malware Linked to Chinese Hackers
Cybersecurity researchers on Wednesday shed light on a new sophisticated backdoor targeting Linux endpoints and servers that's believed to be the work of Chinese nation-state actors. Dubbed "RedXOR" by Intezer, the backdoor masquerades as a polkit daemon, with...
Tracking Users Online – JavaScript Disabled
Researchers have discovered a new side-channel that they say can be reliably exploited to leak information and tracking users from web browsers that could then be leveraged to track users even when JavaScript is completely disabled. "This is a side-channel attack...
ObliqueRAT Payload Hidden by Hacklers
Cybercriminals are now deploying remote access Trojans (ObliqueRAT) under the guise of seemingly innocuous images hosted on infected websites, once again highlighting how threat actors quickly change tactics when their attack methods are discovered and exposed...
Microsoft Exchange Zero-Day Flaws Exploited
Microsoft has released emergency patches to address four previously undisclosed security flaws in Exchange Server that it says are being actively exploited by a new Chinese state-sponsored threat actor with the goal of perpetrating data theft. Describing the attacks...
Chrome Zero-day Bug Under Active Attack
Exactly a month after patching an actively exploited zero-day flaw in Chrome, Google today rolled out fixes for yet another zero-day vulnerability in the world's most popular web browser that it says is being abused in the wild. Chrome 89.0.4389.72, released by the...
ThreatNeedle Malware Targeted
A prolific North Korean state-sponsored hacking group has been tied to a new ongoing espionage campaign aimed at exfiltrating sensitive information from organizations in the defense industry through ThreatNeedle malware. Attributing the attacks with high confidence to...
CNAME Cloaking Technique Used by Trackers
Called CNAME Cloaking, the practice of blurring the distinction between first-party and third-party cookies not only results in leaking sensitive private information without users' knowledge and consent but also "increases [the] web security threat surface," said a...
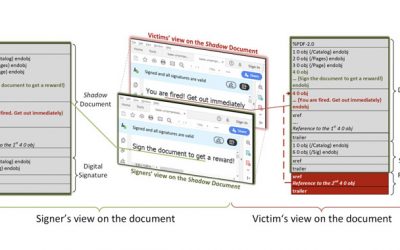
Shadow Attacks – Replacing Content in PDFs
Called "Shadow attacks" by academics from Ruhr-University Bochum, the technique uses the "enormous flexibility provided by the PDF specification so that shadow documents remain standard-compliant." The findings were presented yesterday at the Network and Distributed...
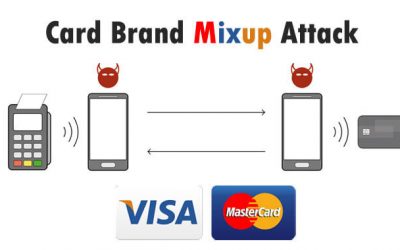
Mastercard Mix-up Attack form Hackers
Cybersecurity researchers have disclosed a novel attack that could allow criminals to trick a point of sale terminal into transacting with a victim's Mastercard contactless card while believing it to be a Visa card. The research, published by a group of academics from...
SolarWinds Hackers Steal Microsoft Code
Microsoft on Thursday said it concluded its probe into the SolarWinds hack, finding that the attackers stole some source code but confirmed there's no evidence that they abused its internal systems to target other companies or gained access to production services or...
IT Monitoring Tool Exploited by Hackers
Russia-linked state-sponsored threat actor known as Sandworm has been linked to a three-year-long stealthy operation to hack targets by exploiting an IT monitoring tool called Centreon. The intrusion campaign — which breached "several French entities" — is said to...
Liquid Video Technologies –
Solutions to Fit Your Budget
Liquid Video Technologies offers solutions that are designed to secure your investment in people, equipment, inventory, and eliminate potential frivolous claims. Whether you need to secure a business location or your home, Liquid Video Technologies has a solution to fit your budget. If you need any additional information or would like to speak with one of our Security Specialists, please call (864) 859-9848 or email us at info@liquidvideotechnologies.com






Recent Comments