Networking News
Liquid Video Technologies, Inc. is here to help you. Not understanding the services we provide or need more information on other matters? These blog posts are here to help you and keep you up-to-date.
Keeping Kids Safe Online
“Here Be Dragons”, Keeping Kids Safe Online Sitting here this morning sipping my coffee, I watched fascinated as my 5-year-old daughter set up a VPN connection on her iPad while munching on her breakfast out of absent-minded necessity. It dawned on me that, while...
Information Security Practices
If An Infosec Policy Falls In The Forest When you are building an Information Security practice you need a solid governance structure in place. For those of you who might not be familiar we can look at it a more accessible way. If you are building a house you need a...
Cybersecurity Risks Identified
Malware And Malicious Insiders Accounted For One-Third Of All Cybercrime Costs Last Year, According To Report From Accenture And Ponemon Institute. The cost to companies from malware and “malicious insider”-related cyberattacks jumped 12 percent in 2018 and accounted...
New Privacy for Facebook
A New Privacy Constitution for Facebook Facebook is making a new and stronger commitment to privacy. Last month, the company hired three of its most vociferouscritics and installed them in senior technical positions. And on Wednesday, Mark Zuckerberg wrote that the...
Is somebody watching you?
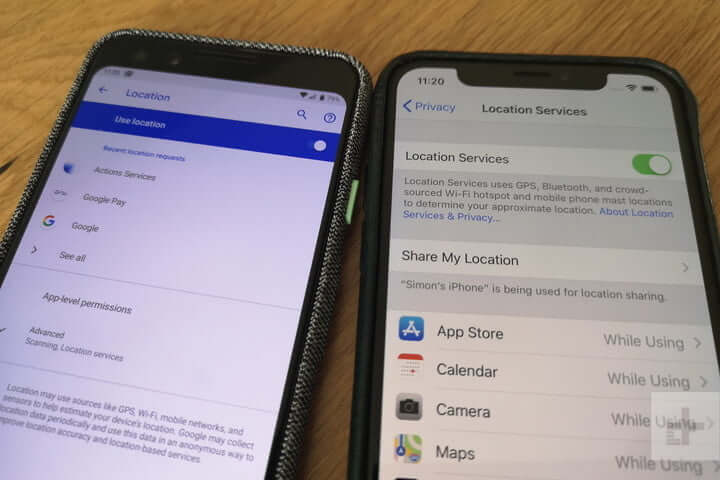
Is somebody watching you? How to stop apps from tracking your location Data on your location and movements is coveted by all sorts of companies. Advertisers want to hit precisely the right demographic in the right location, retailers want to know what stores you visit...
Google confirms it tracks users
Google tracks your location — even when you deny it permission Google confirms it still tracks users who turn Location History off Google is tracking your location — even when you tell it not to, according to an investigation by the Associated Press. The...
Organizational Approach to Cyber Culture
Organizational Approach to Cyber Culture Predictions aren't easy, especially in the chaotic world of cybersecurity. The threat landscape is ever-growing, all thanks to offensive and defensive technologies and nation-state attacks emerging at a fanatic pace with...
Daylight Saving Time Starts Sunday
REMEMBER! Mar 10, 2019 -Daylight Saving Time Starts When local standard time is about to reach Sunday, March 10, 2019, 2:00:00 am clocks are turned forward 1 hour to Sunday, March 10, 2019, 3:00:00 am local daylight time instead. Sunrise and sunset will be about 1...
Is your technology spying on you?
Google Says Unlisted, Built-In Microphone on Nest Devices Wasn't Supposed to Be 'Secret' It’s barely two months into 2019, but Nest has already had a bit of a year. After some hacking scares involving its line of home security cameras, Nest’s latest headache...
Secure Your WiFi Connection
How to Secure Your WiFi Connection Public WiFi can be a lifesaver when you’re working or traveling. But if your device isn’t secure, a hacker could steal passwords, form data, and even work out where you live. Fortunately, it’s easy to protect yourself against the...
Wendy’s $50M data breach
Wendy’s has agreed to pay $50 million to settle negligence claims following its 2015-2016 data breach that affected more than 1,000 of the burger chain’s locations. Payment card data was stolen from victims who purchased food at these locations then used fraudulently...
Avoiding Online Shopping Scams
Avoiding Online Shopping Scams The Internet has made it simple and seamless to visit an online retail store, browse through its goods by the dozen, add one or two products of your choice to a shopping cart, and click to buy. But with simplicity comes bigger...
Online Safety Guide for Kids
The Complete Online Privacy and Safety Guide for Kids The internet, good as it may be, poses a lot of danger to kids and adults alike. The greater risk is however to kids who naturally don’t know much about the darker side of things, but only what makes them happy. In...
How to tell if you’ve Been Cryptojacked
Cryptojacking is the malicious use of a victim’s computer to mine cryptocurrency, and is a growing problem for both individual users and companies. If you’ve never heard of it before, that’s likely because - up until recently -cryptojacking was a fairly niche concern....
Liquid Video Technologies –
Solutions to Fit Your Budget
Liquid Video Technologies offers solutions that are designed to secure your investment in people, equipment, inventory, and eliminate potential frivolous claims. Whether you need to secure a business location or your home, Liquid Video Technologies has a solution to fit your budget. If you need any additional information or would like to speak with one of our Security Specialists, please call (864) 859-9848 or email us at info@liquidvideotechnologies.com













Recent Comments