Networking News
Liquid Video Technologies, Inc. is here to help you. Not understanding the services we provide or need more information on other matters? These blog posts are here to help you and keep you up-to-date.
Election Official Highlights Email Threat
US Election Security Official Highlights Email Threat SANTA FE, N.M. (AP) — Beware the phishing attempts. An election security official with the U.S. Department of Homeland Security on Tuesday warned top state election officials nationwide to safeguard against...
Microsoft Adds an Extra Security Layer
Microsoft Adds an Extra Security Layer to its OneDrive Storage Service Microsoft today announced OneDrive Personal Vault, a new security layer on top of its OneDrive online file storage service that adds additional security features to keep your files save. The...
Increase in Abuse of File Sharing Services
Security researchers are warning of a “dramatic” increase in the exploitation of legitimate file sharing services to deliver malware in email-based attacks, especially OneDrive. FireEye claimed in its latest Email Threat Report for Q1 2019 that services including...
5 Keys to Improve Your Cybersecurity
Cybersecurity isn't easy. If there was a product or service you could buy that would just magically solve all of your cybersecurity problems, everyone would buy that thing, and we could all rest easy. However, that is not the way it works. Technology continues to...
Video Surveillance and the Evolving Needs
Video Surveillance and the Evolving Needs of the End-User: Update, Integrate, Analyze, Act Video surveillance has long been a critical component of facility management and security plans, and it is only expected to grow. Being able to use this video surveillance...
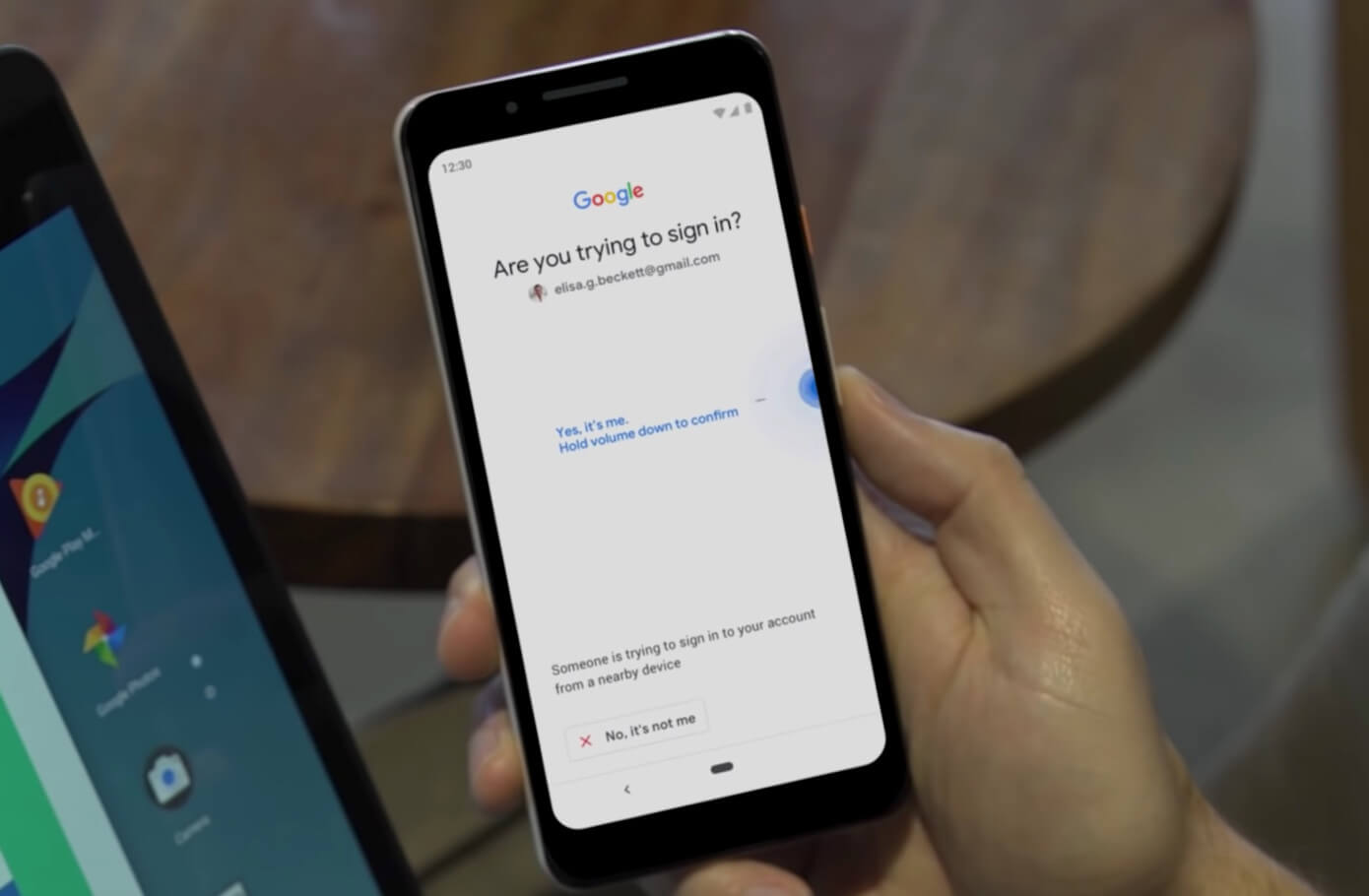
Google Opens its Android Security Key Tech
Google Opens its Android Security-Key Tech to iPhone and iPad Users Google will now allow iPhone and iPad owners to use their Android security key to verify sign-ins, the company said Wednesday. Last month, the search and mobile giant said it developed a new...
3 U.S. Universities Disclose Data Breach
Three U.S. Universities Disclose Data Breaches Over Two-Day Span Three U.S. universities have disclosed data breach incidents impacting personally identifiable information of students or employees following unauthorized access to some of their employees' email...
US Mobile Banking Apps Have Security Flaws
Most US mobile banking apps have security and privacy flaws, researchers say You might figure the biggest U.S. banks would have some of the most secure mobile apps. Spoiler alert: not so much. New findings from security firm Zimperium, shared exclusively with...
Android Users Plagued By Pop-Ups
440 Million Android Users Plagued By Extremely Obnoxious Pop-Ups The mobile ad plugin, found in hundreds of Google Play apps, uses well-honed techniques from malware development to hide itself. Over 440 million Android phones have been exposed to an obnoxious...
Cisco Fixes High Severity Flaws
Cisco Fixes High Severity Flaws in Industrial, Enterprise Tools Cisco patched two high severity improper input validation vulnerabilities found in the update feature of the Cisco Industrial Network Director (IND) software and the authentication service of Cisco...
Apple Security Protections Are Bypassed
Apple MacOS Security Protections Can Easily Bypassed with 'Synthetic' Clicks, Researcher Finds A security researcher has disclosed a new flaw that undermines a core macOS security feature designed to prevent apps — or malware — from accessing a user’s private data,...
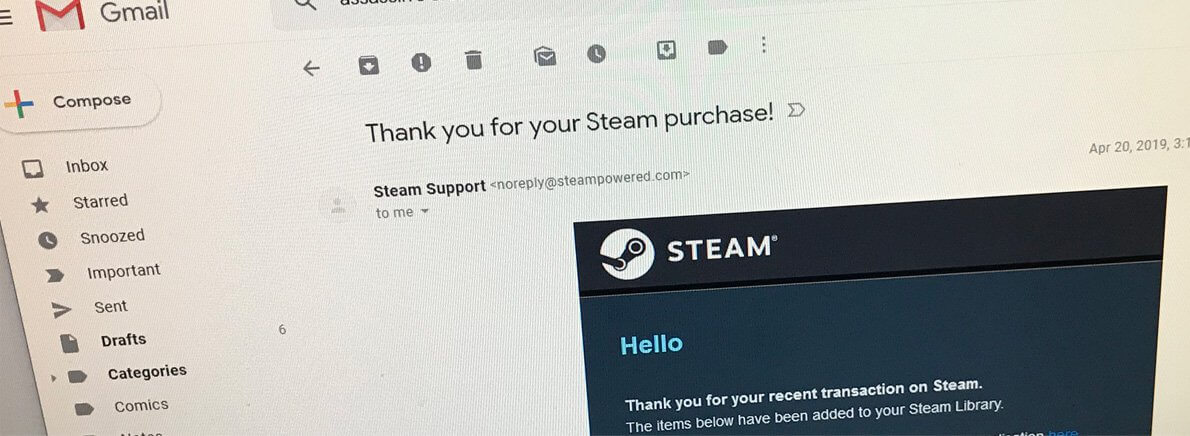
Google is using Gmail to Track Purchases
Google is using Your Gmail Account to Track Your Purchases Do you think your email on Gmail is private? If so, you may want to think again, as your Gmail messages are being scanned by Google for purchases, which are then displayed in your Google account. This week, a...
A Way to Improve Network Security
Scientists May Have Identified a New Way to Improve Network Security With cybersecurity one of the nation’s top security concerns and billions of people affected by breaches last year, government and businesses are spending more time and money defending against it....
Thailand Passes Cybersecurity Law
Thailand passes controversial cybersecurity law that could enable government surveillance Thailand’s government passed a controversial cybersecurity bill today that has been criticized for vagueness and the potential to enable sweeping access to internet user data....
Liquid Video Technologies –
Solutions to Fit Your Budget
Liquid Video Technologies offers solutions that are designed to secure your investment in people, equipment, inventory, and eliminate potential frivolous claims. Whether you need to secure a business location or your home, Liquid Video Technologies has a solution to fit your budget. If you need any additional information or would like to speak with one of our Security Specialists, please call (864) 859-9848 or email us at info@liquidvideotechnologies.com












Recent Comments