Networking News
Liquid Video Technologies, Inc. is here to help you. Not understanding the services we provide or need more information on other matters? These blog posts are here to help you and keep you up-to-date.
Criminals Arrested after Hacking Chat Network
In a joint operation, European and British law enforcement agencies recently arrested hundreds of alleged drug dealers and other criminals after infiltrating into a global network of an encrypted chatting app that was used to plot drug deals, money laundering,...
Joker Malware Apps Spread via Play Store
Malware Apps Cyber security researchers took the wraps off yet another instance of Android malware hidden under the guise of legitimate applications to stealthily subscribe unsuspecting users for premium services without their knowledge. In a report published by Check...
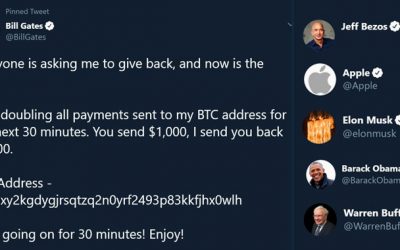
Biggest Twitter Hack of All Time
Social media platform Twitter recently was on fire after it suffered one of the biggest cyber attacks in its history. A number of high-profile Twitter accounts, including those of US presidential candidate Joe Biden, Amazon CEO Jeff Bezos, Bill Gates, Elon Musk, Uber,...
Zoom Flaw let Fraudsters Mimic Organizations
In a report, researchers at cyber security firm CheckPoint today disclosed details of a minor but easy-to-exploit flaw they reported in Zoom, the highly popular and widely used video conferencing software. The latest Zoom flaw could have allowed attackers mimic an...
Android Malware Steals Data from Apps
Cyber security researchers uncovered a new strain of banking malware that targets not only banking apps but also steals data and credentials from social networking, dating, and cryptocurrency apps—a total of 337 non-financial Android applications on its target list....
Application Security is an Enabler for Business
If you ask Alex, he won't admit being old-fashioned. He has been working in the IT industry for a while now and accepts that security is important for the business's health. But reluctant to take security as the business enabler. In today's environment, moving to...
Chinese Hackers Escalate Attacks
An emerging threat actor out of China has been traced to a new hacking campaign aimed at government agencies in India and residents of Hong Kong intending to steal sensitive information, cyber security firm Malwarebytes revealed in the latest report. The attacks were...
How to Fortify Your Cloud Security
With the spread of COVID-19, businesses have faced new challenges. Needless to say, many enterprises are rethinking how they’ve been doing work and what that work will look like. In fact, according to Fugue’s recent State of Cloud Security Survey, 83% of companies...
Cyber Security – Remote Workers are more Security Conscious
Remote workers have become significantly more cyber security conscious since the COVID-19 lockdown began, according to a new study from Trend Micro. It found that nearly three-quarters (72%) of remote workers are more aware of their organization’s cyber security...
Site Hackers Stealing Credit Card Info
In what's one of the most innovative hacking campaigns, cyber crime gangs are now hiding malicious code implants in the metadata of image files to covertly steal credit card information entered by visitors on the hacked websites. "We found skimming code hidden within...
New Ransomware Targeting macOS Users
Cyber security researchers discovered a new type of ransomware targeting macOS users that spreads via pirated apps. According to several independent reports from K7 Lab malware researcher Dinesh Devadoss, Patrick Wardle, and Malwarebytes, the ransomware variant —...
Balancing security and innovation in a crisis
The rapid global shift to a remote workforce and increased reliance on digital infrastructure was met almost immediately by a staggering uptick in cyber crime. With security resources and budgets stretched thin to accommodate remote workforces, cyber criminals were...
Understanding the needs of IoT security
Humans like patterns. We also like trends, labels and buzzwords. We like to fit our problems into a category that can be easily solved by one answer and when this can’t be done, the labels by which we categorize our problems become more and more complex. The Internet...
3 Ways Hackers Get Around Authentication
The cracks in the online security dam keep appearing, and there are only so many fingers left to plug them. Despite living in the most technologically-advanced era in human history, large-scale data breaches continue to grow in intensity and frequency. According to a...
Liquid Video Technologies –
Solutions to Fit Your Budget
Liquid Video Technologies offers solutions that are designed to secure your investment in people, equipment, inventory, and eliminate potential frivolous claims. Whether you need to secure a business location or your home, Liquid Video Technologies has a solution to fit your budget. If you need any additional information or would like to speak with one of our Security Specialists, please call (864) 859-9848 or email us at info@liquidvideotechnologies.com













Recent Comments