Networking News
Liquid Video Technologies, Inc. is here to help you. Not understanding the services we provide or need more information on other matters? These blog posts are here to help you and keep you up-to-date.
Cybersecurity: Securing Internal Environment
Ensuring the cybersecurity of your internal environment when you have a small security team is challenging. If you want to maintain the highest security level with a small team, your strategy has to be 'do more with less,' and with the right technology, you can...
Breached Passwords: Protecting Users
There is no question that attackers are going after your sensitive account data. Passwords have long been a target of those looking to compromise your environment. Why would an attacker take the long, complicated way if they have the keys to the front door? No matter...
Data-Driven Cybersecurity Risk Assessment
Business continuity strategies were put to the test when millions of organizations across the world were suddenly forced to take their workforce to a fully remote environment in response to the COVID-19 pandemic. While many businesses have successfully adapted to...
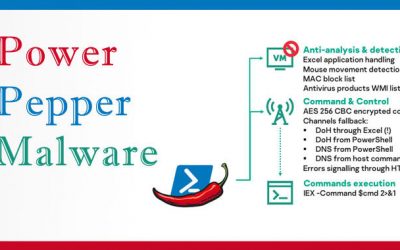
PowerPepper: In-Memory Malware
Cybersecurity researchers on Thursday disclosed details of a previously undiscovered in-memory Windows backdoor developed by a hacker-for-hire operation that can execute remotely malicious code and steal sensitive information from its targets in Asia, Europe, and the...
Hackers Target Covid-19 Vaccine Distribution
A global spear-phishing campaign has been targeting organizations associated with COVID-19 vaccine distribution since September 2020, according to new research. Attributing the operation to a nation-state actor, IBM Security X-Force researchers said the attacks took...
The Best Smart Home Devices for 2021
What Is Smart Home Technology? What if all the devices in your life could connect to the internet? Not just computers and smartphones, but everything: clocks, speakers, lights, doorbells, cameras, windows, window blinds, hot water heaters, appliances, cooking...
FireEye Cybersecurity Firm Got Hacked
FireEye, one of the largest cybersecurity firms in the world, said on Tuesday it became a victim of a state-sponsored attack by a "highly sophisticated threat actor" that stole its arsenal of Red Team penetration testing tools it uses to test the defenses of its...
Steam Server Bugs Left Games Vulnerable
Critical flaws in a core networking library powering Valve's Steam online gaming functionality could have allowed malicious actors to remotely crash games and even take control over affected third-party game servers. "An attacker could remotely crash an opponent's...
Identity Governance: Evaluating Solutions
Enterprises are grappling with increased complexity as cloud adoption increases, the perimeter expands, and digital transformation projects take hold. The accelerated shift to remote working has only added to the complexity. As more businesses leverage hybrid IT...
Zebrocy Malware Delivered Using COVID Bait
A Russian threat actor known for its malware campaigns has reappeared in the threat landscape with yet another attack leveraging COVID-19 as phishing lures, once again indicating how adversaries are adept at repurposing the current world events to their advantage....
Using MSPs to Establish Basic Cyber Hygiene
Small and medium organizations can face a variety of IT challenges: insufficient funding, constantly evolving technologies, growing legal and regulatory requirements, and a lack of skilled and trained IT employees. Oftentimes, these enterprises rely on third-parties...
Cisco Reissues Jabber Software Bug Patches
Cisco has once again fixed four previously disclosed critical bugs in its Jabber video conferencing and messaging app that were inadequately addressed, leaving its users susceptible to remote attacks. The vulnerabilities, if successfully exploited, could allow an...
Third Party: The risk management blind spot
Safeguarding an organization from cybercrime has become vastly more challenging given how digitized and, as a result, interconnected the world has become. Adding complexity to this already daunting scenario is the fact organizations have become perimeter-less, often...
Baidu Apps Caught Collecting User Data
Two popular Android apps from Chinese tech giant Baidu were temporarily unavailable on the Google Play Store in October after they were caught collecting sensitive user details. The two apps in question—Baidu Maps and Baidu Search Box—were found to collect device...
Liquid Video Technologies –
Solutions to Fit Your Budget
Liquid Video Technologies offers solutions that are designed to secure your investment in people, equipment, inventory, and eliminate potential frivolous claims. Whether you need to secure a business location or your home, Liquid Video Technologies has a solution to fit your budget. If you need any additional information or would like to speak with one of our Security Specialists, please call (864) 859-9848 or email us at info@liquidvideotechnologies.com














Recent Comments