Networking News
Liquid Video Technologies, Inc. is here to help you. Not understanding the services we provide or need more information on other matters? These blog posts are here to help you and keep you up-to-date.
Wi-Fi Home Security Alarms Attacked
New vulnerabilities have been discovered in Fortress S03 Wi-Fi Home Security System that could be potentially abused by a malicious party to gain unauthorized access with an aim to alter system behavior, including disarming the deceives without the victim's knowledge....
MTA-STS Improve Your Email Security
Simple Mail Transfer Protocol or SMTP has easily exploitable security loopholes. Email routing protocols were designed in a time when cryptographic technology was at a nascent stage (e.g., the defacto protocol for email transfer, SMTP, is nearly 40 years old now), and...
Microsoft and Google $30 Billion Investment
Google and Microsoft said they are pledging to invest a total of $30 billion in cybersecurity advantages over the next five years, as the U.S. government partners with private sector companies to address threats facing the country in the wake of a string of...
Cybercrime Asking Insiders to Plant Malware
A Nigerian cybercrime threat actor has been observed attempting to recruit employees by offering them to pay $1 million in bitcoins to deploy Black Kingdom ransomware on companies' networks as part of an insider threat scheme. At the beginning of October, a cybercrime...
IoT Devices Spied on Through SDK Bug
A security vulnerability has been found affecting several versions of ThroughTek Kalay P2P Software Development Kit (SDK), which could be abused by a remote attacker to take control of an affected IoT device and potentially lead to remote code executions. The issue...
Malicious Ads Target Cryptocurrency
A new social engineering-based malvertising campaign targeting Japan has been found to deliver malicious ads that deploy a banking trojan on compromised Windows machines to steal credentials associated with cryptocurrency accounts. Malicious ads attack are not a new...
Touchless Security – New Security Buzzword
Much of what people do on daily basis involves touching hundreds of items without thought - we turn to a doorknob to open a door, touch a keypad to type on a computer and push elevator buttons to close the door and select a floor. Until recently, people didn't have to...
Ransomware Prevention Tactics
News and commentary on ransomware have hit a fever pitch with recent, high-profile attacks against global software management provider Kaseya, gas supplier Colonial Pipeline, popular Cape Cod ferry service, The Steamship Authority, and JBS, the world's largest meat...
Insider Threat – Just as Dangerous as Hackers
Among the problems stemming from our systematic failure with cybersecurity, which ranges from decades-old software-development practices to Chinese and Russian cyber-attacks, one problem gets far less attention than it should - the insider threat. "Insiders are the...
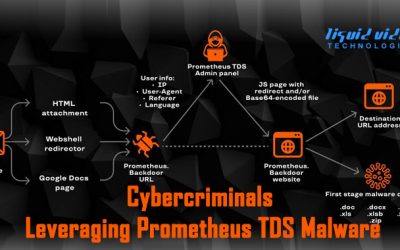
Cybercriminals Leveraging Prometheus TDS
Multiple cybercriminals are leveraging a malware-as-a-service (MaaS) solution to distribute a wide range of malicious software distribution campaigns that result in the deployment of payloads such as Campo Loader, Hancitor, IcedID, QBot, Buer Loader, and SocGholish...
Video Surveillance – A Business Priority
Most business owners or operators know they need some type of video surveillance - whether it's for inventory protection, IT servers holding sensitive data, or managing day-to-day operations, security is an essential part of running a business. For those who've been...
Alarm Systems – How They Communicate
There are many options for how your alarm systems will communicate with the monitoring station. Unfortunately, many homeowners and business owners put very little thought into the different alarm system communication technologies that are available and how these...
Call Centers Trick Users – Install Ransomware
An ongoing malicious campaign that employs phony call centers has been found to trick victims into downloading malware capable of data exfiltrations as well as deploying ransomware on infected systems. This campaign is based in India and has been active since last...
Haron and BlackMatter – Ransomware Gang
Two new ransomware-as-services (RaaS) programs have appeared on the threat radar this month. These two groups are known as BlackMatter and Haron, and although they are not verified, their emergence is not surprising to anyone who was paying attention. It's a bit...
Liquid Video Technologies –
Solutions to Fit Your Budget
Liquid Video Technologies offers solutions that are designed to secure your investment in people, equipment, inventory, and eliminate potential frivolous claims. Whether you need to secure a business location or your home, Liquid Video Technologies has a solution to fit your budget. If you need any additional information or would like to speak with one of our Security Specialists, please call (864) 859-9848 or email us at info@liquidvideotechnologies.com














Recent Comments