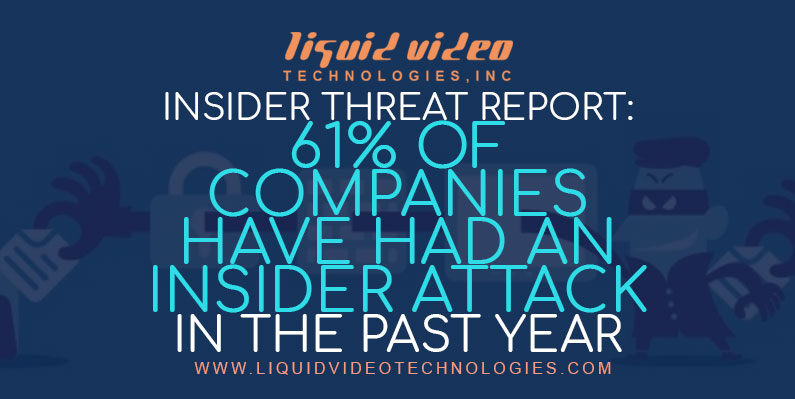
by Liquid Video Technologies | Oct 2, 2020 | Cybersecurity, Data Breaches, Network Security, Security, Security Breach
A Ponemon Institute study of more than 700 IT and security practitioners around the world found that the risk posed by insider threats is growing year-over-year, costing organizations significant money and resources as the threats continue to be difficult to detect,...

by Liquid Video Technologies | Sep 30, 2020 | Access Control, Cybersecurity, Data Breaches, Mobile Access Control, Network Security, Security, Security Breach, Technology News
An Iranian hacker group known for targeting government, defense technology, military, and diplomacy sectors is now impersonating journalists to approach targets via LinkedIn and WhatsApp and infect their devices with malware. Detailing the new tactics of the...
by Liquid Video Technologies | Sep 28, 2020 | Cybersecurity, Data Breaches, Network Security, Security, Security Breach
Cisco has warned of an active zero-day vulnerability in its IOS XR router software that’s being exploited in the wild and could allow a remote, authenticated attacker to carry out memory exhaustion attacks on an affected device. “An attacker could exploit...
by Liquid Video Technologies | Sep 25, 2020 | Access Control, Central Monitoring, Cybersecurity, Data Breaches, Network Security, Security, Security Breach
Internet of Things According to IDC, by 2025 there will be 41.6 billion Internet of Things (IoT) devices, generating a massive 79 zettabytes (ZB) of data. To put that into perspective, in 2006, IDC estimated that the total amount of electronic data created and stored...
by Liquid Video Technologies | Sep 23, 2020 | Access Control, Cybersecurity, Data Breaches, Network Security, News, Security, Security Breach
The United States Cybersecurity and Infrastructure Security Agency (CISA) has published a new report warning companies about a new in-the-wild malware that North Korean hackers are reportedly using to spy on key employees at government contracting companies. Dubbed...
by Liquid Video Technologies | Sep 21, 2020 | Cybersecurity, Data Breaches, Network Security, Security, Security Breach, Uncategorized, Websites
An unpatched security weakness in Google Drive could be exploited by malware attackers to distribute malicious files disguised as legitimate documents or images, enabling bad actors to perform spear-phishing attacks comparatively with a high success rate. The latest...





Recent Comments