An Iranian hacker group known for targeting government, defense technology, military, and diplomacy sectors is now impersonating journalists to approach targets via LinkedIn and WhatsApp and infect their devices with malware.
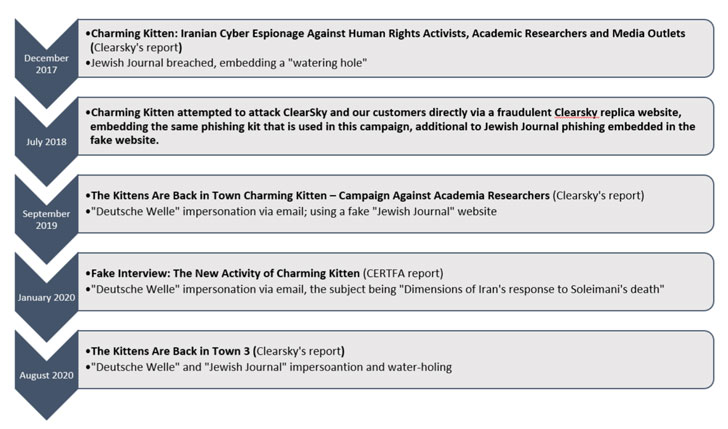
Detailing the new tactics of the “Charming Kitten” APT group, Israeli firm Clearsky said, “starting July 2020, we have identified a new TTP of the group, impersonating ‘Deutsche Welle’ and the ‘Jewish Journal’ using emails alongside WhatsApp messages as their main platform to approach the target and convince them to open a malicious link.”
This development is the first time the threat actor is said to have carried out a watering hole attack through WhatsApp and LinkedIn, which also includes making phone calls to victims, Clearsky noted in a Thursday analysis.
After the company alerted Deutsche Welle about the impersonation and the watering hole in their website, the German broadcaster confirmed, “the reporter which Charming Kitten impersonated did not send any emails to the victim nor any other academic researcher in Israel in the past few weeks.”
Charming Kitten (also known by aliases APT35, Parastoo, NewsBeef, and Newscaster) has been previously linked to a series of covert campaigns at least since December 2017 with an aim to steal sensitive information from human rights activists, academic researchers, and media outlets.
The watering hole — in this case, a malicious link embedded in the compromised Deutsche Welle domain — delivered the info-stealer malware via WhatsApp, but not before the victims were first approached via tried-and-tested social engineering methods with an intention to lure the academics to speak at an online webinar.
“The correspondence began with an email sent to the target, initiating a conversation,” Clearsky explained. “After a short conversation with the target, the Charming Kitten attacker requests to move the conversation to WhatsApp. If the target refuses to move to WhatsApp, the attacker will send a message via a fake LinkedIn profile.”
In one scenario, the adversary even took the step of messaging and calling a victim to gain the target’s trust and subsequently walk the person through the steps of connecting to the webinar using the malicious link earlier shared in the chat.
Although APT35 may have picked up a new ruse, this is not the first time the Iranian hacker group has used social media channels to spy on personnel of interest.
In a three-year-long “Operation Newscaster” uncovered by iSIGHT Partners (now owned by FireEye) in 2014, the threat actor was found to have created false Facebook accounts and a fake news website to spy on military and political leaders in the U.S., Israel, and other countries.
“In this campaign, we observed a willingness of the attackers to speak on the phone directly with the victim, using WhatsApp calls, and a legitimate German phone number. This TTP is uncommon and jeopardizes the fake identity of the attackers,” Clearsky researchers said.
Article Provided By: The Hacker News
![]()
If you would like liquidvideotechnologies.com to discuss developing your Home Security System, Networking, Access Control, Fire, IT consultant or PCI Compliance, please do not hesitate to call us at 864-859-9848 or you can email us at deveren@liquidvideotechnologies.com.


Recent Comments