Networking News
Liquid Video Technologies, Inc. is here to help you. Not understanding the services we provide or need more information on other matters? These blog posts are here to help you and keep you up-to-date.
HTTP Request Smuggling
A new research has identified four new variants of HTTP request smuggling attacks that work against various commercial off-the-shelf web servers and HTTP proxy servers. Amit Klein, VP of Security Research at SafeBreach who presented the findings today at the Black Hat...
How CISOs Can Effectively Measure and Report Security Operations Maturity
The 2019 World Economic Forum Global Report outlined the biggest global risks, ranking data theft and cyberattacks as the fourth and fifth top risks in terms of likelihood. Within the past year alone, more than one-third of US companies reported having suffered a data...
Heightened Fraud and Cyber Risks
As consumers increasingly turn to online shopping for essential and non-essential goods while at home, fraudsters have adapted their technique to use more sophisticated tactics against consumers, banks and merchants. The situation is tenuous. A recent study from...
Security Protocols for a Remote Workforce
It’s an elementary principle of risk management that you should design systems to withstand not just the best possible circumstances, but also the worst. It’s why structures are designed to withstand storms or earthquakes, not just days when Mother Earth is feeling...
Cyber Security on the Modern Battlefield
Chess is a strategic board game estimated to be over 1000 years old. The sharp-mindedness and tactical nous required to win this game was originally designed to mirror medieval battlefield tactics, and the pieces used today reflect this. In a modern context, this...
Websites Provide Hackers with Customer Data
Tala Security has released its Global Data at Risk - 2020 State of the Web Report. The study, which analyzed the security posture of the Alexa top 1000 websites, reveals a troubling lack of security controls required to prevent data theft and loss through client-side...
COVID-19: Moving to a Touchless Future
March 2020 will forever be remembered as the month where the world changed. In a matter of days, the COVID-19 virus closed borders, shuttered businesses and forced people to remain in their homes. The virus also brought with it another threat—cyber security threats....
Adapting Online Security to the Ways we Work
COVID-19 has tested our ability to pivot quickly how we work and where we work. The national workforce has shifted from in-the-office to online virtually overnight. The good news is that those of us who can work remotely have adapted reasonably well, with 29...
Protecting Endpoints in Hybrid Work Environments
Since COVID-19 forced global workforces to go remote, the number of cyber crimes reported to the FBIs Internet Crime Complaint Center (IC3) has spiked from 1,000 a day before the pandemic to as many as 4,000 a day in the last four months. This begs the question, what...
Essential Steps for Protecting Websites
Businesses of all sizes have a lot on their plate when they create and maintain websites. This includes making sure the site is easy to use for visitors, that content is current, that all links work, that the site is optimized for SEO, that e-commerce processes are...
Thermal Imaging Cameras Help Facilities Reopen
To limit the spread of the highly contagious COVID-19 virus, many businesses across the globe have deployed social distancing requirements, stringent cleaning protocols and capacity limitations as part of their plan to safely reopen. Even with these measures in place,...
Chinese Hackers Target COVID-19 Research
The U.S. Department of Justice (DoJ) revealed charges against two Chinese nationals for their alleged involvement in a decade-long hacking spree targeting dissidents, government agencies, and hundreds of organizations in as many as 11 countries. The...
Microsoft Releases Urgent Windows Update
Microsoft quietly released out-of-band software updates to patch two high-risk security vulnerabilities affecting hundreds of millions of Windows 10 and Server editions' users. To be noted, Microsoft rushed to deliver patches almost two weeks before the upcoming...
Critical Apache Flaws Put Desktops at Risk
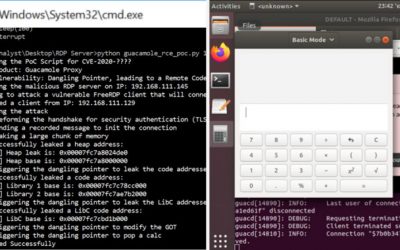
A new research has uncovered multiple critical reverse RDP vulnerabilities in Apache Guacamole, a popular remote desktop application used by system administrators to access and manage Windows and Linux machines remotely. The reported flaws could potentially let bad...
Liquid Video Technologies –
Solutions to Fit Your Budget
Liquid Video Technologies offers solutions that are designed to secure your investment in people, equipment, inventory, and eliminate potential frivolous claims. Whether you need to secure a business location or your home, Liquid Video Technologies has a solution to fit your budget. If you need any additional information or would like to speak with one of our Security Specialists, please call (864) 859-9848 or email us at info@liquidvideotechnologies.com














Recent Comments