
by Liquid Video Technologies | Jul 28, 2021 | Biometrics, Business, Cybersecurity, Hacker, Home Security, Malware, Monitoring, Network Security, Ransomware, Security, zero trust
Organizations today must give attention to their cybersecurity posture, including policies, procedures, and technical solutions for cybersecurity challenges. One key factor is the password policy. This post discusses problems with end-user password change requests and...

by Liquid Video Technologies | Jul 26, 2021 | Business, Central Monitoring, Cybersecurity, Data Breaches, Hacker, Home Security, Malware, Network Security, Security, Security Breach, Websites
A software package available from the official NPM repository has been revealed to be actually a front for a tool that’s designed to steal saved passwords from the Chrome web browser. It demonstrated this ability by automatically prompting the user to reset...
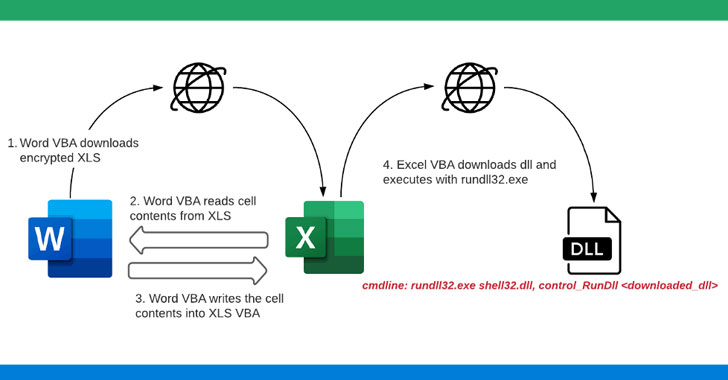
by Liquid Video Technologies | Jul 14, 2021 | Cybersecurity, Hacker, Home Protection, Home Security, Https, Malware, Monitoring, Network Security, Security, Security Breach
While it’s a norm for phishing campaigns that distribute weaponized Microsoft Office documents to prompt users to enable macros in order to directly trigger the infection chain, recent findings now show attackers are using non-malicious documents to disable...

by Liquid Video Technologies | Jul 9, 2021 | API, Cybersecurity, Home Security, Network Security, Security, Websites
Securing applications it the API-first era can be an uphill battle. As development accelerates, accountability becomes unclear, and getting controls to operate becomes a challenge in itself. It’s time that we rethink our application security strategies to...

by Liquid Video Technologies | Jun 25, 2021 | Business, Cloud-Based Access Control, Cybersecurity, Data Breaches, Hacker, Home Protection, Home Security, Malware, Monitoring, Network Security, Security, Security Breach, Technology News
The President released the “Executive Order on Improving the Nation’s Cybersecurity” in response to the malicious actors targeting US federal IT systems and their supply chain. The EO is intended to modernize and strengthen the cybersecurity of...
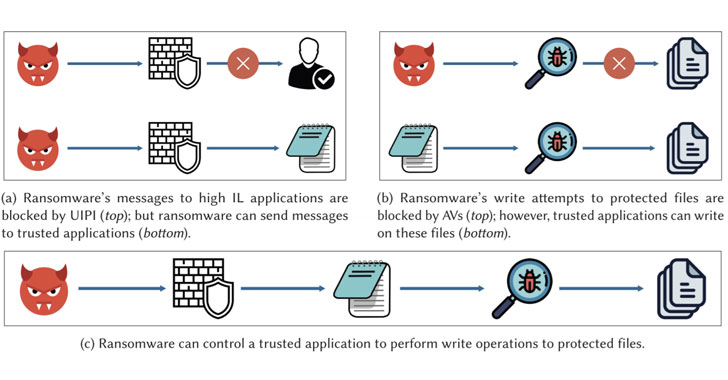
by Liquid Video Technologies | Jun 18, 2021 | Access Control, Business, Cybersecurity, Data Breaches, Hacker, Home Protection, Home Security, Malware, Network Security, Networking, Ransomware, Security, Websites
Researchers have disclosed significant security weaknesses in popular antivirus software solutions applications that could be abused to deactivate their protections and take control of allow-listed applications to perform nefarious operations on behalf of the malware...








Recent Comments