by LVT_Admin | Dec 15, 2021 | Cybersecurity, Hacker, Ransomware, Technology News, Websites
For all you’ve probably heard about Bitcoin, Ethereum, and other cryptocurrencies lately, many financial experts say it’s the technology behind crypto you should really be paying attention to. “The underlying technology that most cryptocurrencies rely on — which is...
by LVT_Admin | Oct 15, 2021 | Business, Hacker, Job Performance, Network Security, Network Video Recorder, Networking
We’ve all heard the advice that networking is important for our careers. And regardless of your profession, your industry or demographic, the message is loud and clear. If you want to be successful, you need to spend time networking. It’s great advice. But the...

by Liquid Video Technologies | Sep 27, 2021 | Access Control, Business, Cybersecurity, Data Breaches, Hacker, Malware, Monitoring, Network Security, Ransomware, Security, Security Breach
Cybersecurity researchers have disclosed a novel technique adopted by a threat actor to deliberately evade detection with the help of malformed digital signatures of its malware payloads. The new mechanism was observed to be exploited by a notorious family of unwanted...

by Liquid Video Technologies | Sep 24, 2021 | Cybersecurity, Data Breaches, Hacker, Malware, Network Security, Security, Security Breach
An “insidious’ new SMS smishing malware has been found targeting Android mobile users in the U.S. and Canada as part of an ongoing campaign that uses SMS text message lures related to COVID-19 regulations and vaccine information in an attempt to steal...
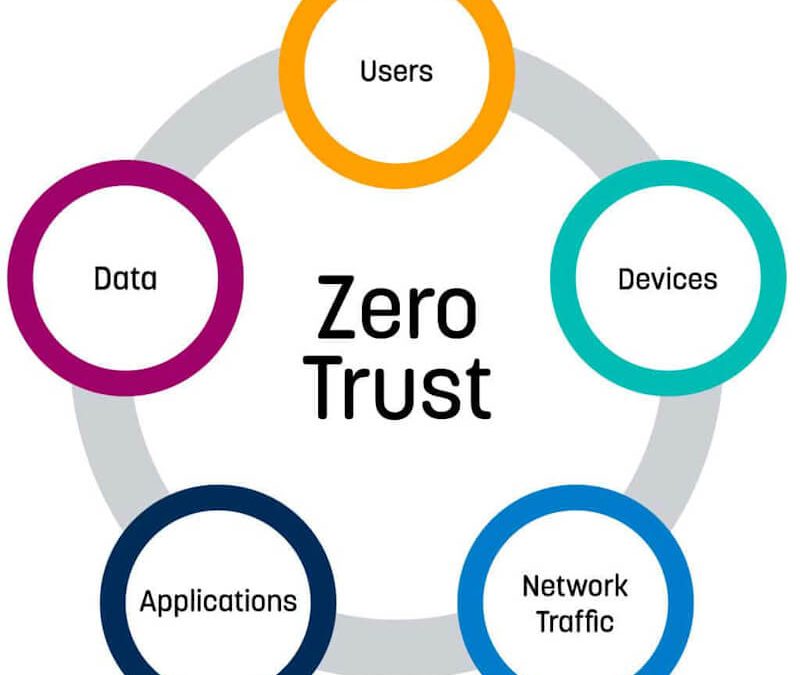
by Liquid Video Technologies | Sep 22, 2021 | Business, Cybersecurity, Data Breaches, Hacker, Home Security, Malware, Security, zero trust
Over the last several years, there have been numerous high-profile security breaches. These breaches have underscored the fact that traditional cyber defenses have become woefully inadequate and that stronger defenses are needed. As such, many organizations have...

by Liquid Video Technologies | Sep 20, 2021 | Business, Cybersecurity, Data Breaches, Hacker, Home Security, Malware, Network Security, Ransomware, Security, Security Breach
Unidentified threat actors breached a server running an unpatched, 11-year-old version of Adobe’s ColdFusion 9 software in minutes to remotely take over control and deploy file-encrypting Cring ransomware on the target’s network 79 hours after the hack....






Recent Comments