Over the last several years, there have been numerous high-profile security breaches. These breaches have underscored the fact that traditional cyber defenses have become woefully inadequate and that stronger defenses are needed. As such, many organizations have transitioned toward a zero-trust security model.
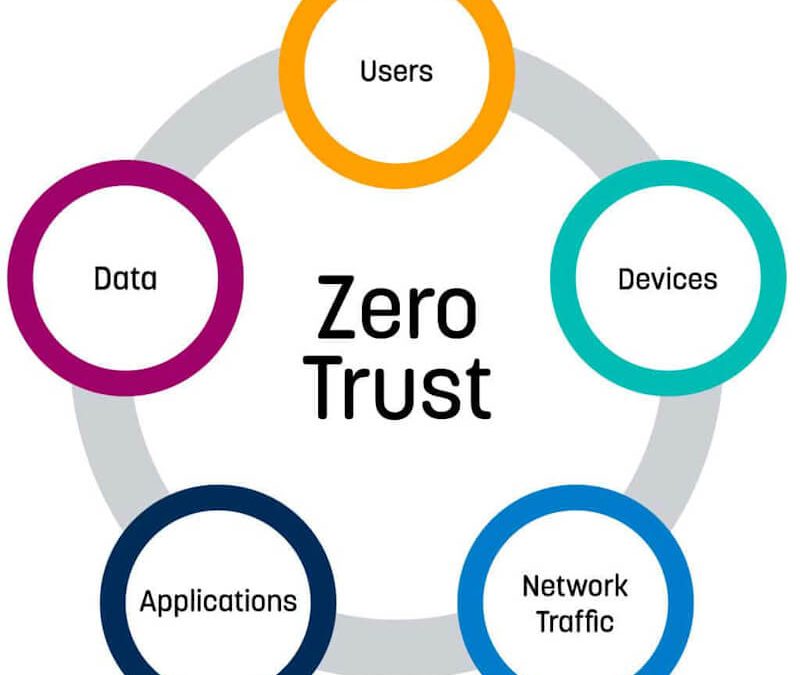
The zero-trust security model is a relatively new approach to security that was developed amid the increase in high-profile data breaches. The model assumes that all users, whether they are internal or external to an organization can’t be trusted. Therefore, if a user’s account is compromised, the security of the entire network is not necessarily impacted. Under this model, administrators will have full control over all of their organization’s connected devices and network applications from a central point located on the corporate network.
This centralized approach allows administrators to segregate access on a granular level for both users and connected devices. All traffic coming into and going out of an organization will be monitored by administrators to ensure that no data leaks occur.
Although the zero-trust model is a relatively new security approach, it is incredibly effective at mitigating damage in the event of a breach. However, many organizations are facing issues in implementing the model. For example, there are numerous challenges associated with segregating all users in one centralized location or segregating users in different locations.
The challenge with segregating all users in one centralized location is that it does not allow for complete information privacy. This means that many usage-based reports could be done against any employee without privacy concerns. For example, you can do payroll checks against all users because you have no privacy concerns when analyzing their activities.
The second challenge with segregating users in different locations is that it is not practical for workspaces that involve collaboration and communication. For example, having a centralized location for all users may result in communication and collaboration issues.
How complicated is it to implement zero-trust within your organization?
Zero-trust security tends to be difficult to implement for several reasons. First, zero-trust security often means operating in a vastly different manner than what IT and the organization’s users are used to. For example, data and applications used by an organization will need to be placed on a centralized server.
This will require a change in behaviors from both IT and end-users. This can prove to be particularly frustrating for those who are used to having the data and applications reside on their own devices or computers. In addition, end-users will likely oppose moving their data to a central, network-based storage system as it is not as user-friendly as what they are accustomed to using. These two problems mean that zero-trust security may not be the best practice for all organizations.
What types of additional security does a zero trust model provide?
While it is sometimes tempting to think of the zero-trust model as being user-centric, zero-trust really means making sure that all actions can be validated and that no actions can be performed without the proper validation.
When an organization uses zero-trust security, it makes sure that there are no username or password breaches. This means that an administrator will have to have the ability to revoke access rights for specific users or groups of users very quickly. It is also the system that will ensure that no data is written unless it has been validated by the system.
How do you ensure your enterprise’s security with zero-trust?
The first step to ensuring your enterprise’s security with zero-trust is performing risk assessments. These assessments should focus on all possible risks and how they may affect your organization. You will want to make sure that you address these risks by implementing appropriate security measures.
In most cases, risk assessments will cost you a large amount of money. However, most security professionals report finding a very significant ROI with cyber security measures. In the event of an attack, these measures will help minimize the damage and will give you a better chance of recovering from a breach.
If your organization is interested in implementing zero-trust security, it is definitely worth exploring your options. Because your organization likely has different needs than others that have already implemented this model, you must make sure that it is the right fit before moving forward. Fortunately, there are many vendors available to help implement zero-trust security for your organization as well as an aftercare program to ensure smooth integration with established operating procedures.
Interested in reading more about zero-trust? Zero-trust Security Model Needed for Email discusses how to implement security needed to secure email using zero-trust.
![]()
If you would like liquidvideotechnologies.com to discuss developing your Home Security System, Networking, Access Control, Fire, IT consultant, or PCI Compliance, please do not hesitate to call us at 864-859-9848 or you can email us at deveren@liquidvideotechnologies.com.

Recent Comments