
by Liquid Video Technologies | Apr 9, 2021 | Cybersecurity, Data Breaches, Security, Security Breach
This appears to be one of the biggest ransomware demands to date, BleepingComputer reports. After inquiries, Acer did not provide a definitive answer if they had suffered a REvil ransomware attack. Instead, they said, “Companies like us are constantly under...

by Liquid Video Technologies | Apr 5, 2021 | Cybersecurity, Data Breaches, Security, Security Breach, zero trust
Google has disclosed that a now-patched vulnerability affecting Android devices that use Qualcomm chipsets is being weaponized by adversaries to launch targeted attacks using the zero-day vulnerability. Tracked as CVE-2020-11261 (CVSS score 8.4), the flaw concerns an...

by Liquid Video Technologies | Apr 2, 2021 | Access Control, Cybersecurity, Data Breaches, Network Security, Security, Security Breach
Cybersecurity researchers on Sunday disclosed multiple critical vulnerabilities in remote student monitoring software Netop Vision Pro that a malicious attacker could abuse to execute arbitrary code and take over Windows computers. “These findings allow for...

by Liquid Video Technologies | Mar 29, 2021 | Cybersecurity, Data Breaches, Security, Security Breach
Cybersecurity researchers on Thursday disclosed a new attack wherein threat actors are leveraging Xcode as an attack vector to compromise Apple platform developers with a backdoor, adding to a growing trend that involves targeting developers and researchers with...
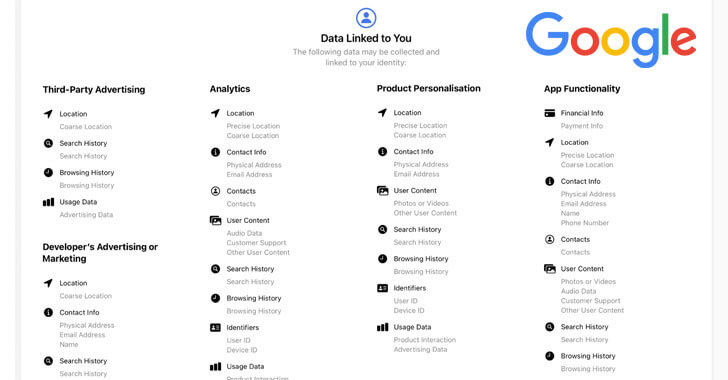
by Liquid Video Technologies | Mar 26, 2021 | Cybersecurity, Data Breaches, Security
Privacy-focused search engine DuckDuckGo called out rival Google for “spying” on users after the search giant updated its flagship app to spell out the exact kinds of information it collects for personalization and marketing purposes. “After months...

by Liquid Video Technologies | Mar 19, 2021 | Cybersecurity, Data Breaches, Security Breach, Technology News
Cybersecurity researchers have discovered a new malware dropper contained in as many as 9 Android apps distributed via Google Play Store that deploys a second stage malware capable of gaining intrusive access to the financial accounts of victims as well as full...








Recent Comments