
by Liquid Video Technologies | Apr 5, 2021 | Cybersecurity, Data Breaches, Security, Security Breach, zero trust
Google has disclosed that a now-patched vulnerability affecting Android devices that use Qualcomm chipsets is being weaponized by adversaries to launch targeted attacks using the zero-day vulnerability. Tracked as CVE-2020-11261 (CVSS score 8.4), the flaw concerns an...

by Liquid Video Technologies | Apr 2, 2021 | Access Control, Cybersecurity, Data Breaches, Network Security, Security, Security Breach
Cybersecurity researchers on Sunday disclosed multiple critical vulnerabilities in remote student monitoring software Netop Vision Pro that a malicious attacker could abuse to execute arbitrary code and take over Windows computers. “These findings allow for...

by Liquid Video Technologies | Mar 31, 2021 | Cybersecurity, Security, Security Breach
A pair of critical vulnerabilities in a popular bulletin board software called MyBB could have been chained together to achieve remote code execution (RCE) without the need for prior access to a privileged account. The flaws, which were discovered by independent...

by Liquid Video Technologies | Mar 29, 2021 | Cybersecurity, Data Breaches, Security, Security Breach
Cybersecurity researchers on Thursday disclosed a new attack wherein threat actors are leveraging Xcode as an attack vector to compromise Apple platform developers with a backdoor, adding to a growing trend that involves targeting developers and researchers with...
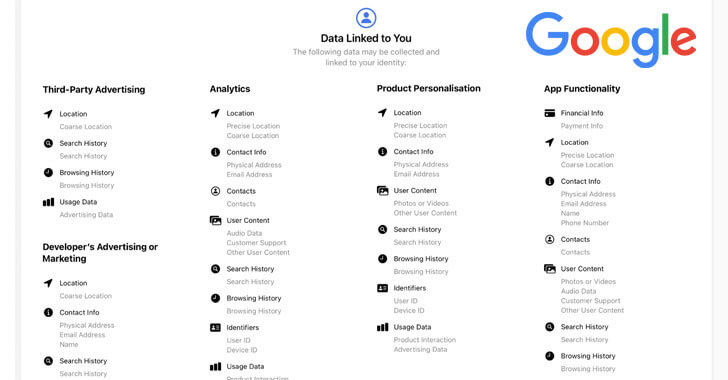
by Liquid Video Technologies | Mar 26, 2021 | Cybersecurity, Data Breaches, Security
Privacy-focused search engine DuckDuckGo called out rival Google for “spying” on users after the search giant updated its flagship app to spell out the exact kinds of information it collects for personalization and marketing purposes. “After months...

by Liquid Video Technologies | Mar 24, 2021 | Cybersecurity, Network Security, Security, Security Breach
Cybersecurity researchers on Monday disclosed a new wave of ongoing attacks exploiting multiple vulnerabilities to deploy new Mirai variants on internet-connected devices. “Upon successful exploitation, the attackers try to download a malicious shell script,...








Recent Comments