Networking News
Liquid Video Technologies, Inc. is here to help you. Not understanding the services we provide or need more information on other matters? These blog posts are here to help you and keep you up-to-date.
Attacks Successfully Hacked Executives
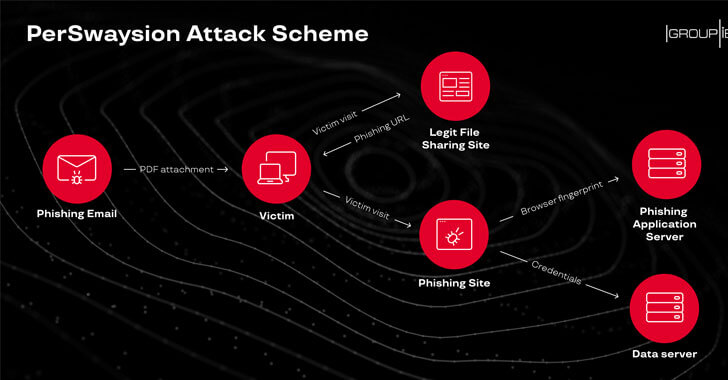
In the last few months, multiple groups of attackers successfully compromised corporate email accounts of at least 156 high-ranking officers at various firms based in Germany, the UK, Netherlands, Hong Kong, and Singapore. Dubbed 'PerSwaysion,' the newly spotted...
Critical Security Patches Released
Software giant Adobe today released emergency updates for three of its widely used products that patch dozens of newly discovered critical vulnerabilities. The list of affected software includes Adobe Illustrator, Adobe Bridge, and Magento e-commerce platform,...
Android Malware Steals Private Banking Data
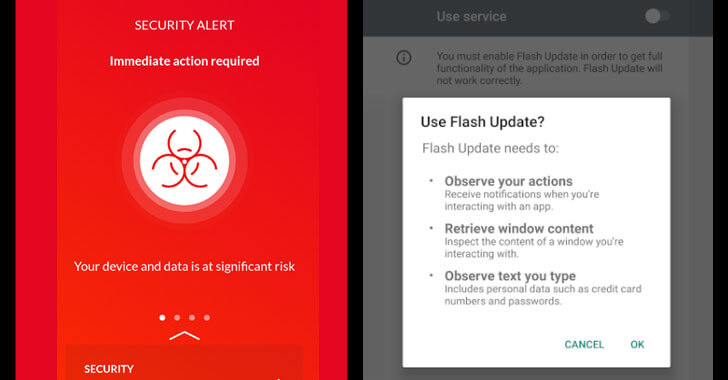
A new type of mobile banking malware has been discovered abusing Android's security features to exfiltrate sensitive data from financial applications, read user SMS messages, and hijack SMS-based two-factor authentication codes. Called "EventBot" by Cybereason...
Expanding Trust in Mobile Devices
For many people, their mobile device, serves as their primary computer in day-to-day life. Modern mobile devices offer a rich, flexible set of features and allow users to add new features just by downloading applications. Users can manage virtually every facet of...
Ransomware Demand Questions to Answer
The landscape of cyber threats is advancing quickly. What used to be an abstract idea and only a concern for “the other guys” is something modern businesses can no longer afford to overlook. Ransomware is a prevailing threat that is quickly taking the spotlight within...
New Security and Privacy Updates for Zoom
Zoom has announced robust security enhancements with the upcoming general availability of Zoom 5.0 as part of their 90-day plan to proactively identify, address and enhance the security and privacy capabilities of the Zoom platform. By adding support for AES 256-bit...
Possible to Hack iPhones by Sending Emails
Watch out Apple users! The default mailing app pre-installed on millions of iPhones and iPads has been found vulnerable to two critical flaws that attackers are exploiting in the wild, at least, from the last two years to spy on high-profile victims. The flaws could...
New Chrome Extensions Caught Hijacking
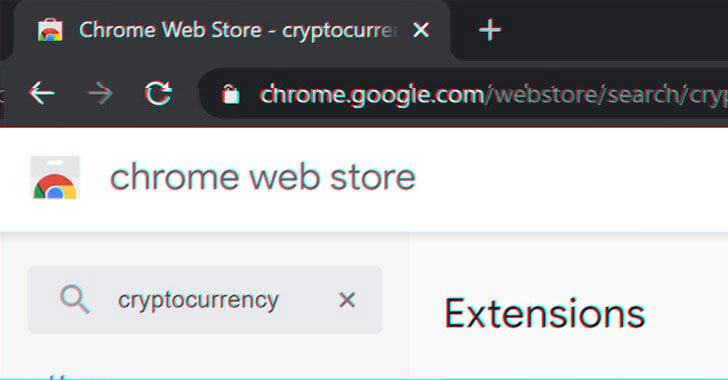
Google has ousted 49 Chrome browser extensions from its Web Store that masqueraded as cryptocurrency wallets but contained malicious code to siphon off sensitive information and empty the digital currencies. The 49 browser add-ons, potentially the work of Russian...
UK Tax Refund Email Scam Uncovered
A newly discovered phishing scam attempts to hook Brits with the promise of a tax refund from Her Majesty's Revenue and Customs. Research published by Abnormal Security details a sophisticated fraud fest in which scammers impersonating the UK government target...
Plan for Minimizing Cybersecurity Failure
While there’s some debate whether Benjamin Franklin or someone else said it first, the advice remains solid for the modern cyber landscape. Yet, in today’s competitive environment, not only is planning critical — but so, too, is planning for plans to fail. Because...
7 Ways Coronavirus Panic is Being Exploited
You might have already read about various campaigns warning how threat actors are capitalizing on the ongoing coronavirus pandemic in an attempt to infect your computers and mobile devices with malware or scam you out of your money. Unfortunately, to some extent, it's...
Marriott Exposes Data of 5.2 Million Guests
International hotel chain Marriott today disclosed a data breach impacting nearly 5.2 million hotel guests, making it the second security incident to hit the company in recent years. "At the end of February 2020, we identified that an unexpected amount of guest...
Zoom Hackers Attack Windows Users
Zoom has been there for nine years, but the immediate requirement of an easy-to-use video conferencing app during the coronavirus pandemic overnight made it one of the most favorite communication tool for millions of people around the globe. No doubt, Zoom is an...
Just Visiting A Site Can Hack Your Camera
If you use Apple iPhone or MacBook, here we have a piece of alarming news for you. Turns out merely visiting a website — not just malicious but also legitimate sites unknowingly loading malicious ads as well — using Safari browser could have let remote attackers...
Liquid Video Technologies –
Solutions to Fit Your Budget
Liquid Video Technologies offers solutions that are designed to secure your investment in people, equipment, inventory, and eliminate potential frivolous claims. Whether you need to secure a business location or your home, Liquid Video Technologies has a solution to fit your budget. If you need any additional information or would like to speak with one of our Security Specialists, please call (864) 859-9848 or email us at info@liquidvideotechnologies.com












Recent Comments