Networking News
Liquid Video Technologies, Inc. is here to help you. Not understanding the services we provide or need more information on other matters? These blog posts are here to help you and keep you up-to-date.
API Lets Developers Authenticate Via SIM
The traditional model of online identity, username/password, has long outlived its usefulness. This is how API multifactor or two-factor authentication has come into play, to patch up vulnerabilities of the so-called knowledge-based model, usually by SMS passcode to...
Ransomware Attack – Steps to Recover
Ransomware attacks are growing in popularity due to their effectiveness to fund malicious activity. As recently, the JBS ransomware attack and the Colonial Pipeline show the extent of attacks that can be implemented. A ransomware attack such as these may fund millions...
Cybersecurity Executive Order 2021
The President released the "Executive Order on Improving the Nation's Cybersecurity" in response to the malicious actors targeting US federal IT systems and their supply chain. The EO is intended to modernize and strengthen the cybersecurity of federal information...
Ransom of $11 Million Paid by JBS to Hackers
JBS, the world's largest meat processing company by sales, paid $11 million in bitcoin to hackers for the purpose of regaining access to its systems following the destructive ransomware attack late last month. However, JBS had to do this in order to recover systems...
TLS Attack Possibly Compromises Secure Site
A new type of attack has emerged that exploits misconfigurations in transport layer security (TLS) servers that can redirect HTTPS traffic from a victim's web browser to a different TLS service endpoint located on another IP address, allowing the sensitive data to be...
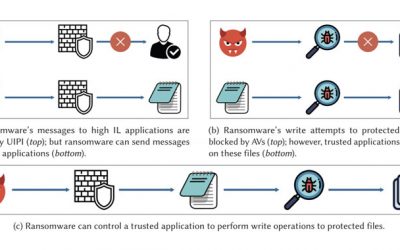
Antivirus Solutions Bypassed by Malware
Researchers have disclosed significant security weaknesses in popular antivirus software solutions applications that could be abused to deactivate their protections and take control of allow-listed applications to perform nefarious operations on behalf of the malware...
Network – Build Flexible, Scalable and Secure
Apps are at the heart of today’s businesses. Organizations increasingly rely on software to create more engaging customer experiences, enhance operational efficiencies and empower remote workers. Apps running in cloud environments, or a network, also help boost...
Email Spoofing – Check Your Domain Security
Are you aware of how secure your domain is? In most organizations, there is an assumption that their domains are secure and within a few months, but the truth soon dawns on them that it isn't and email spoofing may occur. Spotting someone spoofing your domain name is...
Business Hacked – What to Do Next
As businesses move to a remote workforce, hackers have increased their activity to capitalize on new security holes. Cybercriminals often use unsophisticated methods that continue to be extremely successful rendering a business hacked. These include phishing emails to...
Single Sign-On Enough to Secure SaaS
If there's one thing all great SaaS platforms share in common, it's their focus on simplifying the lives of their end-users. Removing friction for users in a safe way is the mission of single sign-on (SSO) providers. With SSO at the helm, users don't have to remember...
Darkside Ransomware Extorts Millions
DarkSide, the hacker group behind the Colonial Pipeline ransomware attack earlier this month, received $90 million in bitcoin payments following a nine-month ransomware spree, making it one of the most profitable cybercrime groups. "In total, just over $90 million in...
Password Hygiene Needs a Reboot
In today's digital world, password security is more important than ever. While biometrics, one-time passwords (OTP), and other emerging forms of authentication are often touted as replacements to the traditional password, today, this concept is more marketing hype...
Executive Order Over U.S. Cybersecurity
U.S. President Joe Biden has signed an executive order, EO, to improve the cybersecurity of the U.S. As the U.S. faces persistent and increasingly sophisticated malicious cyber campaigns that threaten the public sector, the private sector, and ultimately people’s...
Flaws in Latest Security Windows Update
Microsoft on Tuesday rolled out its scheduled monthly security update with patches for 55 security flaws affecting Windows, Exchange Server, Internet Explorer, Office, Hyper-V, Visual Studio, and Skype for Business. Of these 55 bugs, four are rated as Critical, 50 are...
Liquid Video Technologies –
Solutions to Fit Your Budget
Liquid Video Technologies offers solutions that are designed to secure your investment in people, equipment, inventory, and eliminate potential frivolous claims. Whether you need to secure a business location or your home, Liquid Video Technologies has a solution to fit your budget. If you need any additional information or would like to speak with one of our Security Specialists, please call (864) 859-9848 or email us at info@liquidvideotechnologies.com












Recent Comments