
by Liquid Video Technologies | Sep 1, 2021 | Cybersecurity, Data Breaches, Hacker, Home Protection, Home Security, Malware, Monitoring, Network Security, Ransomware, Security, Security Breach, Websites
Simple Mail Transfer Protocol or SMTP has easily exploitable security loopholes. Email routing protocols were designed in a time when cryptographic technology was at a nascent stage (e.g., the defacto protocol for email transfer, SMTP, is nearly 40 years old now), and...

by Liquid Video Technologies | Aug 30, 2021 | Business, Cybersecurity, Data Breaches, Hacker, Home Security, Malware, Network Security, Ransomware, Security, Security Breach, Websites
Google and Microsoft said they are pledging to invest a total of $30 billion in cybersecurity advantages over the next five years, as the U.S. government partners with private sector companies to address threats facing the country in the wake of a string of...

by Liquid Video Technologies | Aug 27, 2021 | Business, Central Monitoring, Cybersecurity, Data Breaches, Hacker, Malware, Network Security, Networking, People That Make A Difference, Ransomware, Security, Security Breach
A Nigerian cybercrime threat actor has been observed attempting to recruit employees by offering them to pay $1 million in bitcoins to deploy Black Kingdom ransomware on companies’ networks as part of an insider threat scheme. At the beginning of October, a...

by Liquid Video Technologies | Aug 18, 2021 | Business, Central Monitoring, Cybersecurity, Data Breaches, Hacker, Home Security, Https, Malware, Monitoring, Network Security, Ransomware, Security, Security Breach, Websites
News and commentary on ransomware have hit a fever pitch with recent, high-profile attacks against global software management provider Kaseya, gas supplier Colonial Pipeline, popular Cape Cod ferry service, The Steamship Authority, and JBS, the world’s largest...
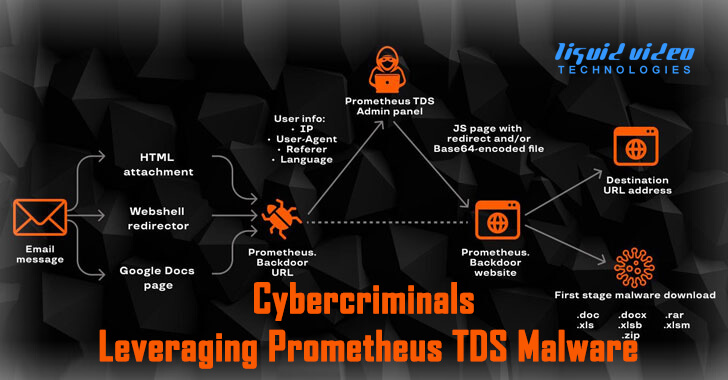
by Liquid Video Technologies | Aug 13, 2021 | Cybersecurity, Hacker, Malware, People That Make A Difference, Ransomware, Security
Multiple cybercriminals are leveraging a malware-as-a-service (MaaS) solution to distribute a wide range of malicious software distribution campaigns that result in the deployment of payloads such as Campo Loader, Hancitor, IcedID, QBot, Buer Loader, and SocGholish...

by Liquid Video Technologies | Aug 6, 2021 | Central Monitoring, Cybersecurity, Data Breaches, Hacker, Home Monitoring, Home Protection, Home Security, Malware, Network Security, Networking, Ransomware, Security, Security Breach
An ongoing malicious campaign that employs phony call centers has been found to trick victims into downloading malware capable of data exfiltrations as well as deploying ransomware on infected systems. This campaign is based in India and has been active since last...








Recent Comments