It’s an easy fix for the consumer, but enterprise customers may need IT’s help to mitigate the risk of issues like URL hijacking
When a computer connects to a public Wi-Fi network or an untrusted LAN, a malicious actor could potentially compromise a browser’s HTTPS connection and eavesdrop on URLs such as Dropbox, Google Drive URLs or Password reset URLs.
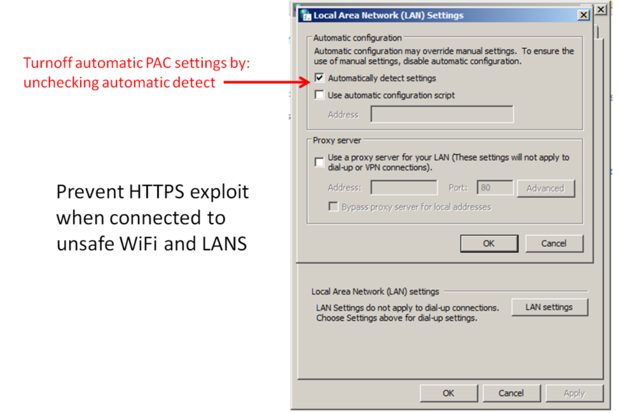
The fix is easy for a consumer: un-checking the automatic detect setting. But an enterprise user might need to ask the IT department to eliminate this risk. Windows, Mac and Linux computers are all at risk.
Windows: How to reduce the risk of URL hijacking
To prevent this HTTPS URL hijacking on a Windows computer, open the Control Panel and select Internet Properties. Then select the Connections Tab, and in it the LAN settings button. Un-check Automatically detect settings.
 Steven Max Patterson
Steven Max Patterson Mac: How to reduce the risk of URL hijacking
On a Mac select the Apple menu then System Preferences, then Network. Select the network service from the list, for example, Ethernet or Wi-Fi. The select Advanced, then finally deselect Proxies.
How the URL hijacking works
Itzik Kotler and Amit Klein of SafeBreach presented a proof of concept at the Black Hat conference yesterday that demonstrated how a web browser can be exploited to exfiltrate (extract) URLs from HTTP, HTTPS and FTP traffic. Users are reassured seeing https:// preceding the URL in their browser bars after the internet industry campaign two years ago to force websites to move from the clear text HTTP protocol to bidirectional SSL/TLS encrypted HTTPS. According to Kotler and Klein, this may not always be true, especially on public Wi-Fi and untrusted LANs
The LAN settings explained above turn on Web Proxy Auto-Discovery (WPAD) that automatically looks for a proxy auto-config (PAC) file that chooses the proxy server that is the intermediary through which the browser traffic flows. Many enterprises use this method to point web browsers and other user agents to the proxy server designated for a group of users. Alternatively, malware could insert a PAC file (proxy.pac) onto a computer with WPAD disabled to accomplish the same hijack. The researchers said it would be difficult for antivirus software to detect this type of attack.
When the infected computer connects to a malicious proxy server, the URLs can be exfiltrated. The collection of URLs extends beyond a violation personal privacy. The researchers said password reset URLs could also be intercepted, which could be initiated by a malicious actor who has some information about a user found on the internet, such as an email address or account information acquired through social engineering.
Although the HTTPS traffic between the user’s browser and the website can’t be read, the exploit could open up a two-way channel between the malicious proxy server, placing the computer at risk of further harm if the malicious actors were able to drop additional malware on the infected computer. This malware could be used in a denial of service attack or to steal data.
Avoiding untrusted networks is the best protection. Connecting to a MiFi or smartphone hotspot or using a VPN to connect through an untrusted network will protect from this threat.
Article Provided By: NetworkWorld
![]()
If you would like liquidvideotechnologies.com to discuss developing your Home Security System, Networking, Access Control, Fire, IT consultant or PCI Compliance, please do not hesitate to call us at 864-859-9848 or you can email us at deveren@liquidvideotechnologies.com


Recent Comments