Cybersecurity researchers on Thursday disclosed details of a previously undiscovered in-memory Windows backdoor developed by a hacker-for-hire operation that can execute remotely malicious code and steal sensitive information from its targets in Asia, Europe, and the US. Dubbed “PowerPepper” by Kaspersky researchers, the malware has been attributed to the DeathStalker group (formerly called Deceptikons), a threat actor that has been found to hit law firms and companies in the financial sector located in Europe and the Middle East at least since 2012.
The hacking tool is so-called because of its reliance on steganographic trickery to deliver the backdoor payload in the form of an image of ferns or peppers.
The espionage group first came to light earlier this July, with most of their attacks starting with a spear-phishing email containing a malicious modified LNK (shortcut) file that, when clicked, downloads and runs a PowerShell-based implant named Powersing.
While their objectives don’t appear to be financially motivated, their continued interest in collecting crucial business information led Kaspersky to the conclusion that “DeathStalker is a group of mercenaries offering hacking-for-hire services, or acting as some sort of information broker in financial circles.”
PowerPepper now joins the group’s list of expanding and evolving toolsets.
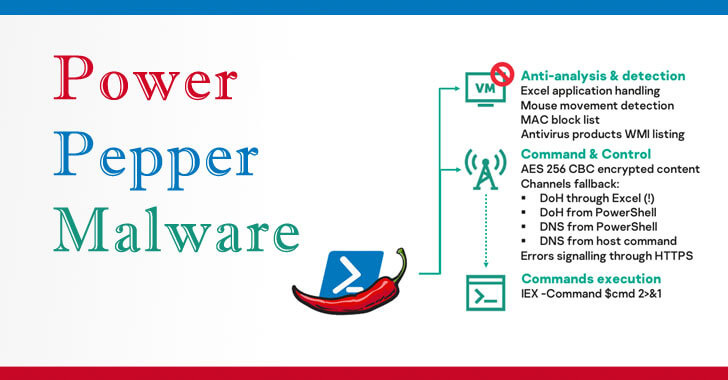
Spotted in the wild in mid-July 2020, this new strain of malware gets dropped from a decoy Word document and leverages DNS over HTTPS (DoH) as a communications channel to transmit encrypted malicious shell commands from an attacker-controlled server.
The spear-phishing emails come with themes as varied as carbon emission regulations, travel booking, and the ongoing coronavirus pandemic, with the Word documents having social engineering banners urging users to enable macros in a bid to lure an unsuspecting user into downloading the backdoor.
To achieve its goals, the implant sends DNS requests to name servers — servers that store the DNS records — associated with a malicious C2 domain, which then sends back the command to be run in the form of an embedded response. Upon execution, the results are beamed to the server through a batch of DNS requests.
Besides leveraging macro-based and LNK-based delivery chains to deploy the malware, DeathStalker employed “obfuscation, execution and masquerading tricks to hinder detection, or deceive targets that are curious about what is happening on their computers,” Kaspersky’s Pierre Delcher noted.
Chief among them are the capabilities to hide malicious execution workflow in Word embedded shape and object properties and use Windows Compiled HTML Help (CHM) files as archives for malicious files.
Multiple mercenary groups have been seen in the wild before, including BellTroX (aka Dark Basin), Bahamut, and CostaRicto, all of whom have deployed custom malware to breach systems belonging to financial institutions and government officials.
“It only seems fair to write that DeathStalker tried hard to develop evasive, creative and intricate tools with this PowerPepper implant and associated delivery chains,” Delcher concluded.
“There is nothing particularly sophisticated about the techniques and tricks that are leveraged, yet the whole toolset has proved to be effective, is pretty well put together, and shows determined efforts to compromise various targets around the world.”
To safeguard against PowerPepper delivery and execution, it is recommended that businesses and users update their CMS backends as well as associated plugins, restrict PowerShell use on end-user computers with enforced execution policies, and refrain from opening Windows shortcuts attached to emails, or click links in emails from unknown senders.
Article Provided By: Hacker News
![]()
If you would like liquidvideotechnologies.com to discuss developing your Home Security System, Networking, Access Control, Fire, IT consultant or PCI Compliance, please do not hesitate to call us at 864-859-9848 or you can email us at deveren@liquidvideotechnologies.com.

Recent Comments