Multiple cybercriminals are leveraging a malware-as-a-service (MaaS) solution to distribute a wide range of malicious software distribution campaigns that result in the deployment of payloads such as Campo Loader, Hancitor, IcedID, QBot, Buer Loader, and SocGholish against individuals in Belgium as well as government agencies, companies, and corporations in the U.S.
A recently published report from Cisco Talos provides details on cybercriminals leveraging the Prometheus TDS malware platform. Initially uncovered by malware researchers in July, the malware is part of the cybercriminals supply chain that allows threat actors to purchase malware capable of mass distribution while hiding their tracks using a variety of obfuscation methods.
Cybercriminals can use the Prometheus TDS platform to develop and conduct extensive infection campaigns without having to deal with the technicalities and maintenance that usually come with building, deploying, and maintaining such operations. One advantage for attackers is they don’t have to worry about integrating all the primary components required for an advanced infection chain, according to Cisco Talos.
“The TDS malware platform provides a highly effective solution for the cybercrime ecosystem. It is a one-stop-shop for all the capabilities required to conduct an advanced infection chain,” researchers explained.
Since we initially covered the discovery of Prometheus TDS in July of this year, Cisco Talos has reported several threat groups leveraging the platform. This article will discuss the most recent campaigns leveraging URL shorteners combined with malicious Microsoft Excel documents to deliver Text Document Script (TDS) malware. Talos’s report provides details on how cybercriminals can execute these attacks and lists indicators of compromise (IoCs).
Fake Scripts, Not Remote Desktop
The threat actors used in the past weeks’ campaigns have been responsible for the following targets:
Belgian government agencies (including government ministries) of the Center for Public Health, Ministry of the Interior, and Ministry of Foreign Affairs; Belgian companies (such as Ertica) and a US company (such as Fastenal). It is worth noting that Syrian intelligence agencies are believed to be present among potential TDS targets. The difference between targets mentioned above and those in previous campaigns is that attackers only used encoded Microsoft Excel documents this time.
The campaigns were able to successfully infect machines at the mentioned Belgian targets in order to deliver various payloads. The payloads included:
- Campo Loader (which delivers a backdoor)
- Hancitor (also known as Loki)
- IcedID (which takes over the infected machine’s webcam, delivers a remote access tool, and steals credentials) – CVE-2016-5271 Exploit Code Name: iced.exe New Vulnerable CVEs for this piece of malware: CVE-2017-0510 and CVE-2017-0511 Exploit Code Name: iced.exe
In order to get a better understanding of how these payloads are delivered, we need to first understand the process of purchasing and ultimately receiving the TDS malware. This begins with the selection of a “builder” within the malware platform. The builder is responsible for creating new variants of code that can be used in attacks.
Once a builder is selected, customers can express their preferences in the form of an options request. TDS attackers specify their preferences when purchasing an attack through various “packages,” which come with a price tag. The packages include the following options:
Standard Package – This option includes a comprehensive set of components that are required to conduct an advanced infection chain.
- This option includes a comprehensive set of components that are required to conduct an advanced infection chain.
Advanced Package – This option is for enterprises and smaller groups needing the most complete set of capabilities provided by the platform, including Web shell functionality and remote access tool (RAT).
- This option is for enterprises and smaller groups needing the most complete set of capabilities provided by the platform, including Web shell functionality and remote access tool (RAT).
Custom Package – The custom package allows customers to customize their package based on their specific needs, resulting in lower prices than those stated for other options.
- The custom package allows customers to customize their package based on their specific needs, resulting in lower prices than those stated for other options.
Team Package – This option includes all the components required to conduct an advanced infection chain, as well as additional functionality such as dropping payload during ATM skimming.
- This option includes all the components required to conduct an advanced infection chain, as well as additional functionality such as dropping payload during ATM skimming.
Multi-Packages. -The multi-packages include two or more packages from the standard and advanced packages for a price that is below that of purchasing them individually.
The attack process begins with the distribution of “scripts” which are actually macros written in VBScript (.vbs or .wsf). An example of a “script” used in this most recent campaign looks as follows:
The script opens three separate Excel spreadsheets, which contain the message for the victim, decoy documents, and the malware itself. If the victim is using Microsoft Office 2007, 2010, or 2013, they will be able to see these files. However, if they are using Office 2016 or the Office viewer then they will not be able to see them. This is because Microsoft has protected these newer versions of Office against malicious macros by prompting users before executing them.
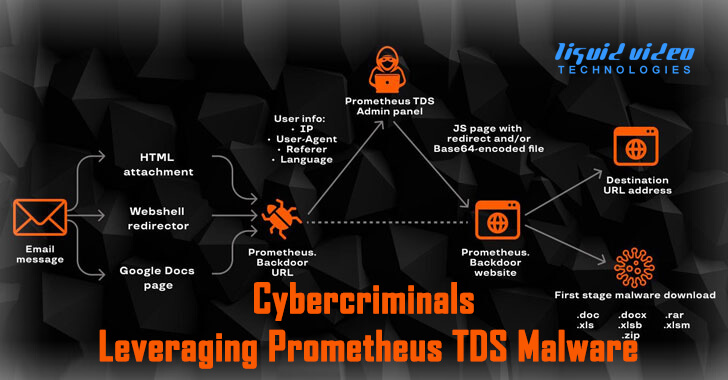
In the final phase, the administrative panel takes responsibility for sending a command to redirect the user to a particular URL, or to send a malware-ridden Microsoft Word or Excel document, with the user redirected to a legitimate site like DocuSign or USPS immediately after downloading the file to mask the malicious activity.
Once the infection has occurred, the attacker can take control of the machine and often install additional malware. Following this activity, attackers will exfiltrate data using a variety of channels, including downloading file archives saved to Dropbox. This specific example is a TDS builder named Mr. Black who was responsible for distributing the attack scripts during this most recent campaign.
Interested in reading more about cybercriminals? Cyber-Attack Groups In Ransomware Web discusses how cybercriminals are all connected through ransomware.
![]()
If you would like liquidvideotechnologies.com to discuss developing your Home Security System, Networking, Access Control, Fire, IT consultant, or PCI Compliance, please do not hesitate to call us at 864-859-9848 or you can email us at deveren@liquidvideotechnologies.com.

Recent Comments