
by Liquid Video Technologies | Jun 30, 2021 | Biometrics, Central Monitoring, Cybersecurity, Hacker, Https, Malware, Network Security, Security, Security Breach
The traditional model of online identity, username/password, has long outlived its usefulness. This is how API multifactor or two-factor authentication has come into play, to patch up vulnerabilities of the so-called knowledge-based model, usually by SMS passcode to...

by Liquid Video Technologies | Jun 28, 2021 | Business, Crime, Drama, Cybersecurity, Data Breaches, Hacker, Malware, Network Security, Ransomware, Security, Security Breach, Websites
Ransomware attacks are growing in popularity due to their effectiveness to fund malicious activity. As recently, the JBS ransomware attack and the Colonial Pipeline show the extent of attacks that can be implemented. A ransomware attack such as these may fund millions...

by Liquid Video Technologies | Jun 25, 2021 | Business, Cloud-Based Access Control, Cybersecurity, Data Breaches, Hacker, Home Protection, Home Security, Malware, Monitoring, Network Security, Security, Security Breach, Technology News
The President released the “Executive Order on Improving the Nation’s Cybersecurity” in response to the malicious actors targeting US federal IT systems and their supply chain. The EO is intended to modernize and strengthen the cybersecurity of...

by Liquid Video Technologies | Jun 23, 2021 | Access Control, Data Breaches, Hacker, Malware, Network Security, Ransomware, Security, Security Breach
JBS, the world’s largest meat processing company by sales, paid $11 million in bitcoin to hackers for the purpose of regaining access to its systems following the destructive ransomware attack late last month. However, JBS had to do this in order to recover...

by Liquid Video Technologies | Jun 21, 2021 | Cybersecurity, Data Breaches, Hacker, Https, Network Security, Networking, Security, Security Breach, Websites
A new type of attack has emerged that exploits misconfigurations in transport layer security (TLS) servers that can redirect HTTPS traffic from a victim’s web browser to a different TLS service endpoint located on another IP address, allowing the sensitive data...
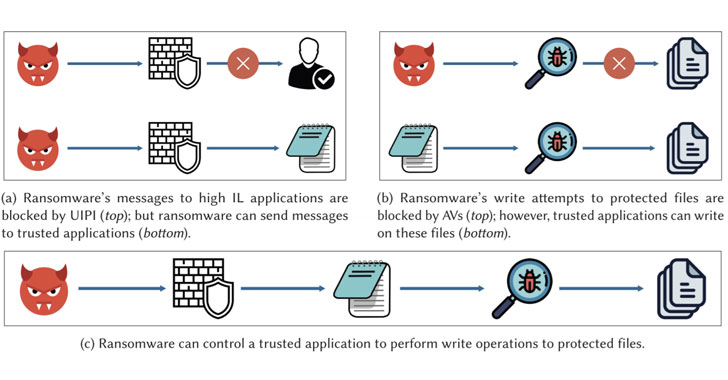
by Liquid Video Technologies | Jun 18, 2021 | Access Control, Business, Cybersecurity, Data Breaches, Hacker, Home Protection, Home Security, Malware, Network Security, Networking, Ransomware, Security, Websites
Researchers have disclosed significant security weaknesses in popular antivirus software solutions applications that could be abused to deactivate their protections and take control of allow-listed applications to perform nefarious operations on behalf of the malware...








Recent Comments