
by Liquid Video Technologies | Jun 21, 2021 | Cybersecurity, Data Breaches, Hacker, Https, Network Security, Networking, Security, Security Breach, Websites
A new type of attack has emerged that exploits misconfigurations in transport layer security (TLS) servers that can redirect HTTPS traffic from a victim’s web browser to a different TLS service endpoint located on another IP address, allowing the sensitive data...
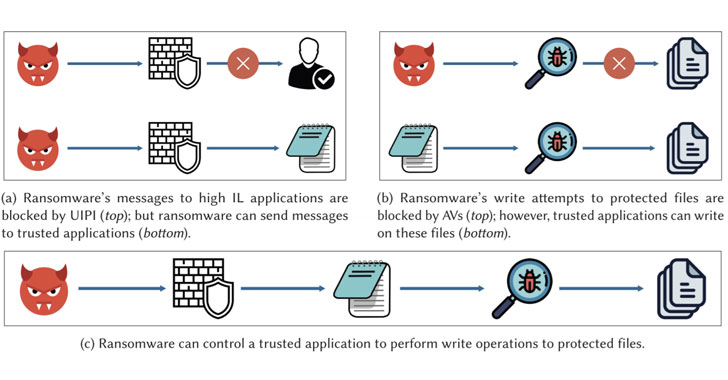
by Liquid Video Technologies | Jun 18, 2021 | Access Control, Business, Cybersecurity, Data Breaches, Hacker, Home Protection, Home Security, Malware, Network Security, Networking, Ransomware, Security, Websites
Researchers have disclosed significant security weaknesses in popular antivirus software solutions applications that could be abused to deactivate their protections and take control of allow-listed applications to perform nefarious operations on behalf of the malware...

by Liquid Video Technologies | Jun 16, 2021 | Access Control, Cloud-Based Access Control, Cybersecurity, Data Breaches, Hacker, Home Security, Malware, Network Security, Networking, Security
Apps are at the heart of today’s businesses. Organizations increasingly rely on software to create more engaging customer experiences, enhance operational efficiencies and empower remote workers. Apps running in cloud environments, or a network, also help boost...

by Liquid Video Technologies | Jun 14, 2021 | Business, Cybersecurity, Data Breaches, Hacker, Network Security, Security, Security Breach
Are you aware of how secure your domain is? In most organizations, there is an assumption that their domains are secure and within a few months, but the truth soon dawns on them that it isn’t and email spoofing may occur. Spotting someone spoofing your domain...

by Liquid Video Technologies | Jun 11, 2021 | Cybersecurity, Data Breaches, Hacker, Malware, Monitoring, Network Security, Networking, PCI Breach, Ransomware, Security, Security Breach
As businesses move to a remote workforce, hackers have increased their activity to capitalize on new security holes. Cybercriminals often use unsophisticated methods that continue to be extremely successful rendering a business hacked. These include phishing emails to...

by Liquid Video Technologies | Jun 9, 2021 | Cybersecurity, Data Breaches, Hacker, Home Monitoring, Home Protection, Home Security, Malware, Monitoring, Network Security, Networking, Security, Security Breach
If there’s one thing all great SaaS platforms share in common, it’s their focus on simplifying the lives of their end-users. Removing friction for users in a safe way is the mission of single sign-on (SSO) providers. With SSO at the helm, users don’t...








Recent Comments