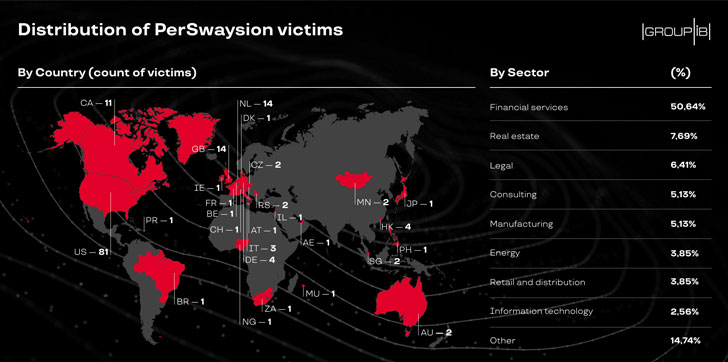
In the last few months, multiple groups of attackers successfully compromised corporate email accounts of at least 156 high-ranking officers at various firms based in Germany, the UK, Netherlands, Hong Kong, and Singapore.
Dubbed ‘PerSwaysion,’ the newly spotted cyberattack campaign leveraged Microsoft file-sharing services—including Sway, SharePoint, and OneNote—to launch highly targeted phishing attacks.
According to a report Group-IB Threat Intelligence team published today and shared with The Hacker News, PerSwaysion operations attacked executives of more than 150 companies around the world, primarily with businesses in finance, law, and real estate sectors.
“Among these high-ranking officer victims, more than 20 Office365 accounts of executives, presidents, and managing directors appeared.”
So far successful and still ongoing, most PerSwaysion operations were orchestrated by scammers from Nigeria and South Africa who used a Vue.js JavaScript framework-based phishing kit, evidently, developed by and rented from Vietnamese speaking hackers.
“By late September 2019, PerSwaysion campaign has adopted much mature technology stacks, using Google appspot for phishing web application servers and Cloudflare for data backend servers.”
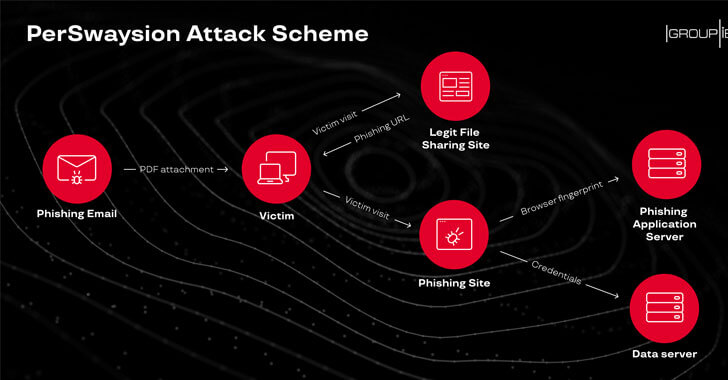
Like most phishing attacks aiming to steal Microsoft Office 365 credentials, fraudulent emails sent as part of PerSwaysion operation also lured victims with a non-malicious PDF attachment containing ‘read now’ link to a file hosted with Microsoft Sway.
“The attackers pick legitimate cloud-based content sharing services, such as Microsoft Sway, Microsoft SharePoint, and OneNote to avoid traffic detection,” the researchers said.
Once stolen, attackers immediately move on to the next step and download victims’ email data from the server using IMAP APIs and then impersonate their identities to further target people who have recent email communications with the current victim and hold important roles in the same or other companies.
“Finally, they generate new phishing PDF files with the current victim’s full name, email address, legal company name. These PDF files are sent to a selection of new people who tend to be outside of the victim’s organization and hold significant positions. The PerSwaysion operators typically delete impersonating emails from the outbox to avoid suspicion.”
“Evidence indicates that scammers are likely to use LinkedIn profiles to assess potential victim positions. Such a tactic reduces the possibility of early warning from the current victim’s co-workers and increases the success rate of new phishing cycle.”
Though there’s no clear evidence on how attackers are using compromised corporate data, researchers believe it can be ‘sold in bulk to other financial scammers to conduct traditional monetary scams.’
Group-IB has also set-up an online web-page where anyone can check if their email address was compromised as part of PerSwaysion attacks—however, you should only use it and enter your email if you’re highly expecting to be attacked.
![]()
If you would like liquidvideotechnologies.com to discuss developing your Home Security System, Networking, Access Control, Fire, IT consultant or PCI Compliance, please do not hesitate to call us at 864-859-9848 or you can email us at deveren@liquidvideotechnologies.com.

Recent Comments