Microsoft Office now the most targeted platform, as browser security improves
Microsoft Office has become cybercriminals’ preferred platform when carrying out attacks, and the number of incidents keeps increasing, Kaspersky Lab researchers said during the company’s annual conference, Security Analyst Summit, in Singapore. Boris Larin, Vlad Stolyarov and Alexander Liskin showed that the threat landscape has changed in the past two years and urged users to keep their software up-to-date and to avoid opening files that come from untrusted sources to reduce the risk of infection.
Today, more than 70% of all the attacks Kaspersky Lab catches are targeting Microsoft Office, and only 14% take advantage of browser vulnerabilities. Two years ago, it was the opposite: Web-based vulnerabilities accounted for 45% of the attacks, while Microsoft Office had a 16% share.
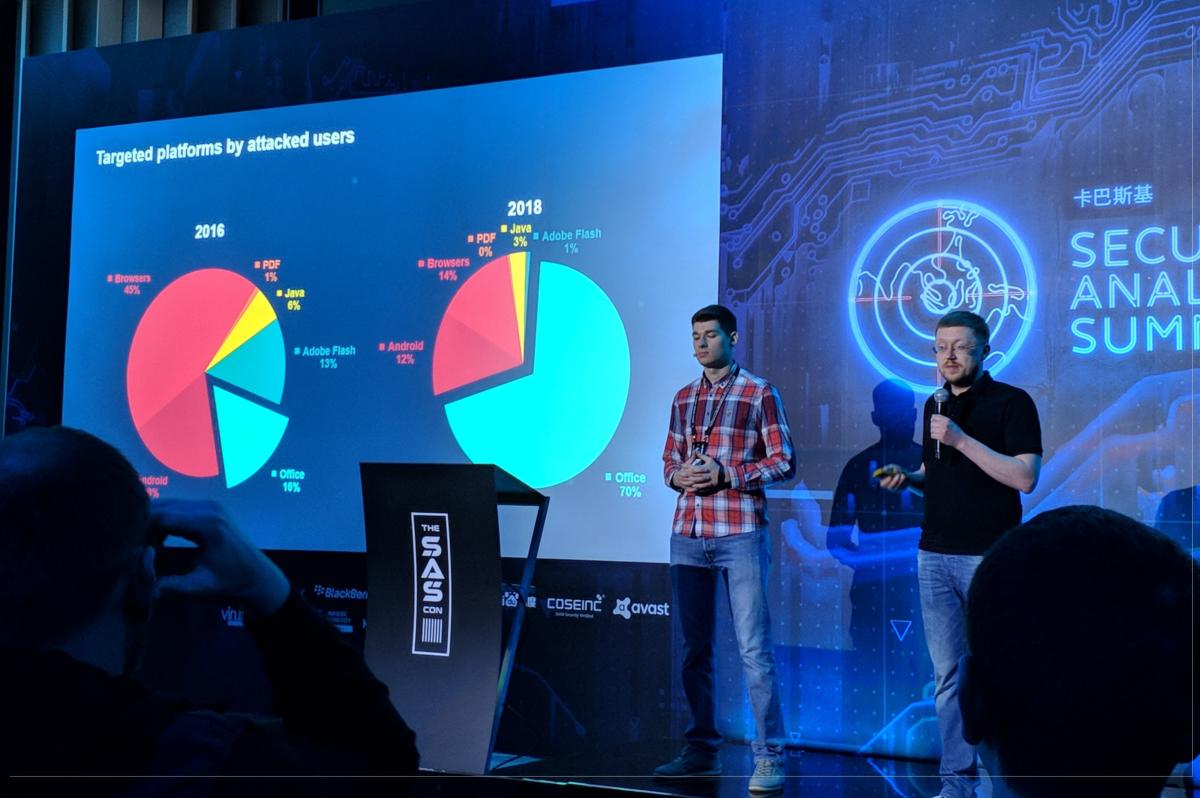
Researchers said that this is because hacking browsers has become more expensive, as browser security has improved. “Browser developers put much effort into different kinds of security protections and mitigations,” Liskin said. “Attackers were looking for a new target, and MS Office has become a star.”
Liskin added that there are plenty of reasons why cybercriminals choose to attack the popular suite. “Microsoft Office has a huge number of different file formats,” he said. “It is deeply integrated into the Windows operating system.”
He also argued that when Microsoft created Office, it made several decisions that, in hindsight, aren’t optimal security-wise and are currently difficult to change. Making such alterations would have a significant impact on all the versions of the products, Liskin said.
The researchers pointed out that the most exploited vulnerabilities from the past two years are not in MS Office itself, but rather in related components. Two of those vulnerabilities, CVE-2017-11882 and CVE-2018-0802, exploit bugs found in Equation Editor. Cybercriminals prefer to use them because they can be found in every version of Microsoft Word released in the past 17 years. Moreover, building exploits for them does not require advanced skilled, because the Equation Editor binary lacks modern protections and mitigations. These are simple, logical vulnerabilities, the researchers said.
Exploit uses Internet Explorer to hack Office
Another interesting vulnerability is CVE-2018-8174. In this unusual case, the vulnerability was actually in Internet Explorer, but the exploit was found in an Office file. “The exploit was delivered as an obfuscated RTF document,” researcher Larin said. “This is the first exploit to use a vulnerability in Internet Explorer to hack Microsoft Office.”
The infection chain has three steps. First, the victim opens the malicious document. As they do this, a second stage of the exploit is downloaded: an HTML page that contains a VBScript code. This then triggers the third step, ause after free (UAF) vulnerability, and executes shellcode. UAF bugs are a type of memory corruption vulnerability that have been very successful in the past for browser exploitation. The technique works by referencing memory after it has been freed, causing the software to crash or allowing an attacker to execute code.
Cybercriminals act fast on Microsoft exploits
What intrigues Larin, Stolyarov and Liskin the most about the cases they’ve studied is how fast cybercriminals operate. Most incidents start with a Microsoft Office zero-day that’s used in a targeted campaign. Once it becomes public, it’s only a matter of days until exploits appear on the dark web. Sometimes, it can even be faster, as has happened with CVE-2017-11882, the first Office Equation Editor vulnerability Kaspersky Lab researchers uncovered. The publication of the proof of concept was followed by a massive spam campaign that began on the very same day.
Microsoft Office vulnerabilities might become even more common in the near future, as attackers continue to target the suite. Larin advised users to keep their software updated, and to pay attention to the files they receive from dubious email addresses. “Our best recommendation is not to open links and files received from untrusted sources, and have installed security solutions with advanced detection of exploits,” Larin added.
![]()
If you would like liquidvideotechnologies.com to discuss developing your Home SecuritySystem, Networking, Access Control, Fire, IT consultant or PCI Compliance, please do not hesitate to call us at 864-859-9848 or you can email us at deveren@liquidvideotechnologies.com.



Recent Comments