Apple MacOS Security Protections Can Easily Bypassed with ‘Synthetic’ Clicks, Researcher Finds
A security researcher has disclosed a new flaw that undermines a core macOS security feature designed to prevent apps — or malware — from accessing a user’s private data, webcam or microphone without their explicit permission.
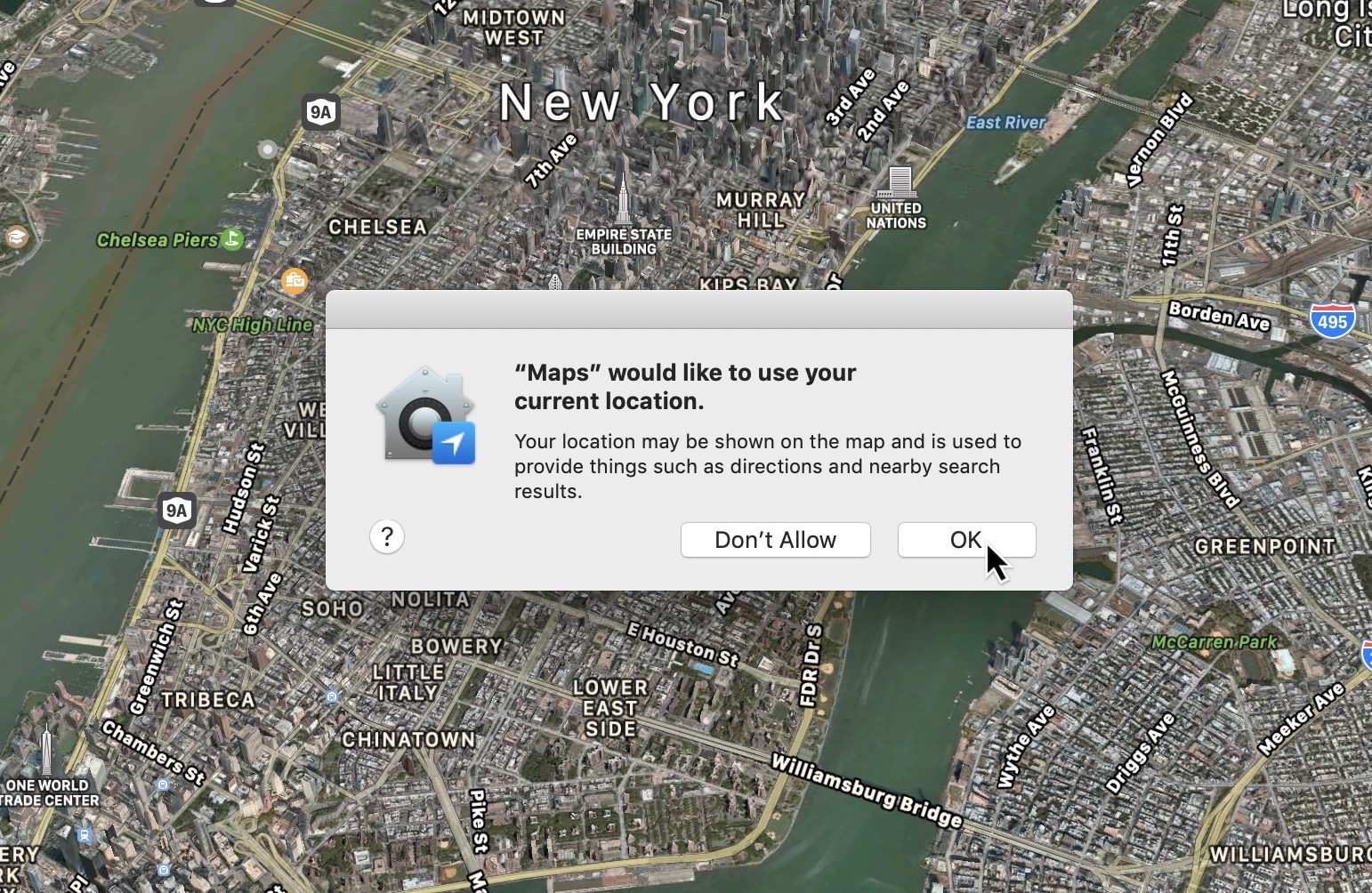
The privacy protections, recently expanded in macOS Mojave, were meant to make it more difficult for malicious apps to get access to a user’s private information — like their contacts, calendar, location and messages — unless the user clicks ‘allow’ on a popup box. The protections are also meant to prevent apps from switching on a Mac’s webcam and microphone without consent. Apple’s Craig Federighi touted the security features as “one of the reasons people choose Apple” at last year’s WWDC developer conference.
But the protections weren’t very good. Those ‘allow’ boxes can be subverted with a maliciously manufactured click.
It was previously possible to create artificial or “synthetic” clicks by using macOS’ in-built automation feature AppleScript, or by using mouse keys, which let users — and malware — control the mouse cursor using the numeric pad on the keyboard. After fixing these bugs in previous macOS versions, Apple’s current defense is to block all synthetic clicks, requiring the user to physically click on a button.
But Patrick Wardle, a former NSA hacker who’s now chief research officer at Digita Security, said he’s found another way to bypass these protections with relative ease.
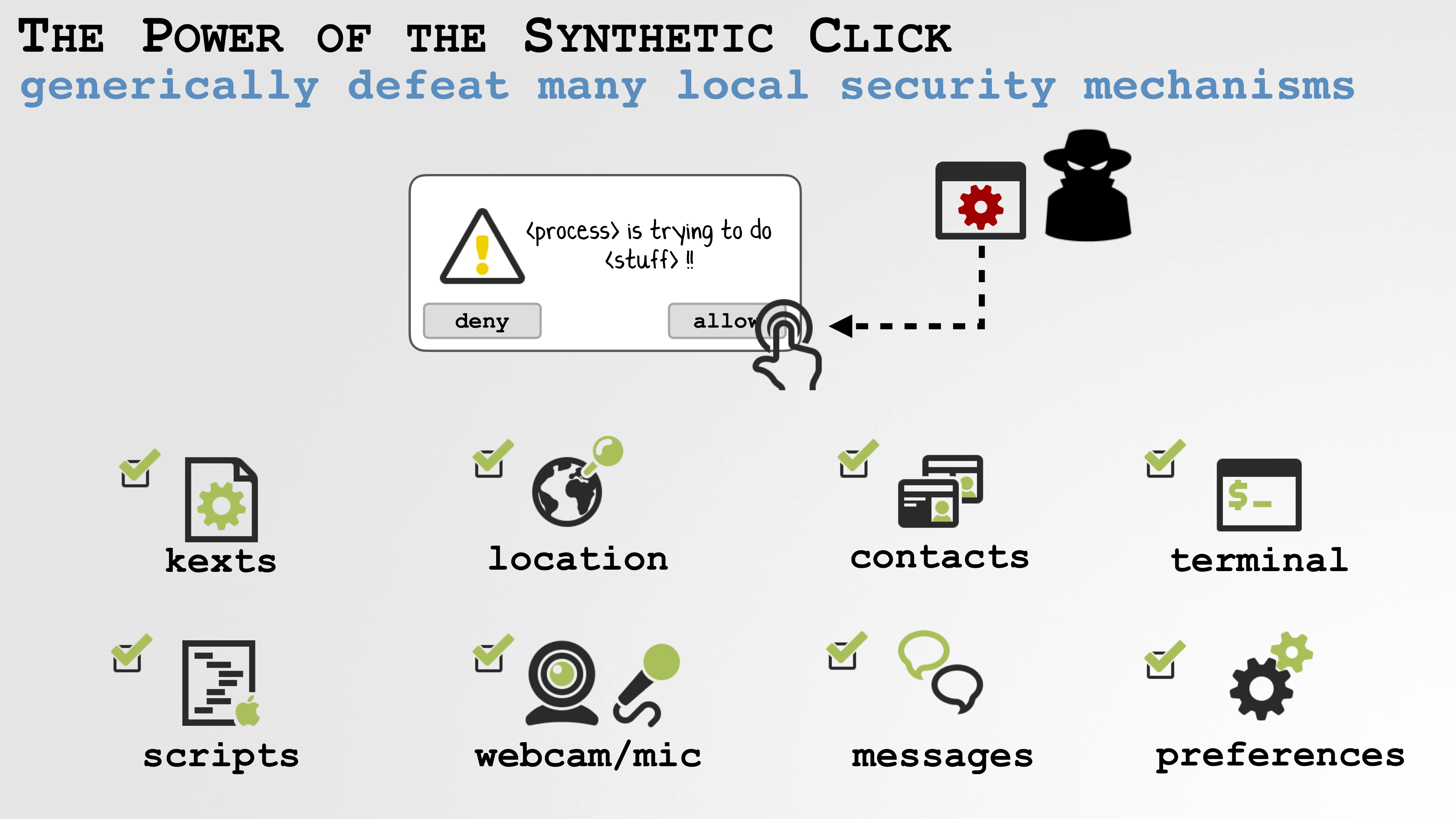
Wardle, who revealed the zero-day flaw at his conference Objective By The Sea in Monaco on Sunday, said the bug stems from an undocumented whitelist of approved macOS apps that are allowed to create synthetic clicks to prevent them from breaking.
Typically apps are signed with a digital certificate to prove that the app is genuine and hasn’t been tampered with. If the app has been modified to include malware, the certificate usually flags an error and the operating system won’t run the app. But a bug in Apple’s code meant that that macOS was only checking if a certificate exists and wasn’t properly verifying the authenticity of the whitelisted app.
“The only thing Apple is doing is validating that the application is signed by who they think it is,” he said. Because macOS wasn’t checking to see if the application had been modified or manipulated, a manipulated version of a whitelisted app could be exploited to trigger a synthetic click.
One of those approved apps is VLC, a popular and highly customizable open-source video player that allows plugins and other extensions. Wardle said it was possible to use VLC as a delivery vehicle for a malicious plugin to create a synthetic click on a consent prompt without the user’s permission.
“For VLC, I just dropped in a new plugin, VLC loads it, and because VLC loads plugins, my malicious plugin can generate a synthetic click — which is fully allowed because the system sees its VLC but doesn’t validate that the bundle to make sure it hasn’t been tampered with,” he explained
“And so my synthetic events is able to click and access the users location, webcam, microphone,” he said.
Wardle describe the vulnerability as a “second stage” attack because the bug already requires an attacker — or malware — to have access to the computer. But it’s exactly these kinds of situations where malware on a computer tries to click through on a consent box that Apple is trying to prevent, Wardle said.
He said he informed Apple of the bug last week but the tech giant has yet to release a patch. “This isn’t a remote attack so I don’t think this puts a large number of Mac users immediately at risk,” he said.
An Apple spokesperson did not return a request for comment.
It’s not the first time Wardle has warned Apple of a bug with synthetic clicks. He reported related bugs in 2015, 2017 and 2018. He said it was “clear” that Apple doesn’t take these bugs seriously.
“In this case, literally no-one looked at this code from a security point of view,” he said.
“We have this undocumented whitelisting feature that is paramount to all these new privacy and security features, because if you can generate synthetic events you can generically thwart them of them trivially,” he said.
“It’s important to get this right,” he said.
Article Provided By: techcrunch
![]()
If you would like liquidvideotechnologies.com to discuss developing your Home SecuritySystem, Networking, Access Control, Fire, IT consultant or PCI Compliance, please do not hesitate to call us at 864-859-9848 or you can email us at deveren@liquidvideotechnologies.com.


Recent Comments