Preying on public fears, the ongoing coronavirus outbreak is proving to be a goldmine of opportunity for attackers to stage a variety of malware attacks, phishing campaigns, and create scam sites and malicious tracker apps.
Now in a fresh twist, third-party Android app developers too have begun to take advantage of the situation to use coronavirus-related keywords in their app names, descriptions, or in the package names so as to drop malware, perpetrate financial theft and rank higher in Google Play Store searches related to the topic.
“Most malicious apps found are bundle threats that range from ransomware to SMS-sending malware, and even spyware designed to clean out the contents of victims’ devices for personal or financial data,” Bitdefender researchers said in a telemetry analysis report.
The find by Bitdefender is the latest in an avalanche of digital threats piggybacking on the coronavirus pandemic.
Using Coronavirus-Related Keywords to Rank in Game Play Store Searches
As people increasingly sought out applications that provided information about COVID-19, malware authors have sneaked in adware, banking trojans (e.g., Anubis, Cerberus, Joker), and information stealers under the guise of live tracker apps and those that help users identify common symptoms of the illness.
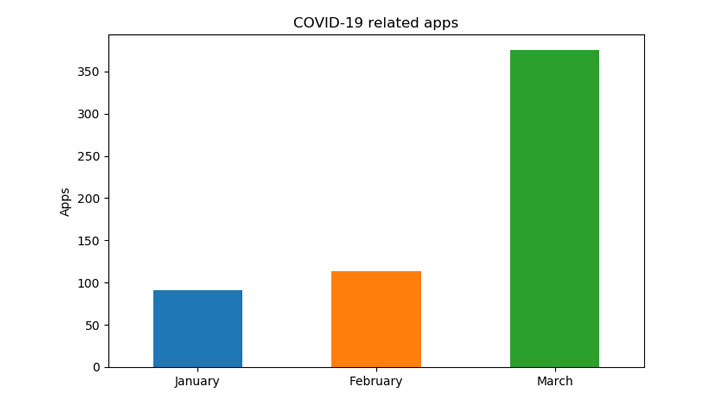
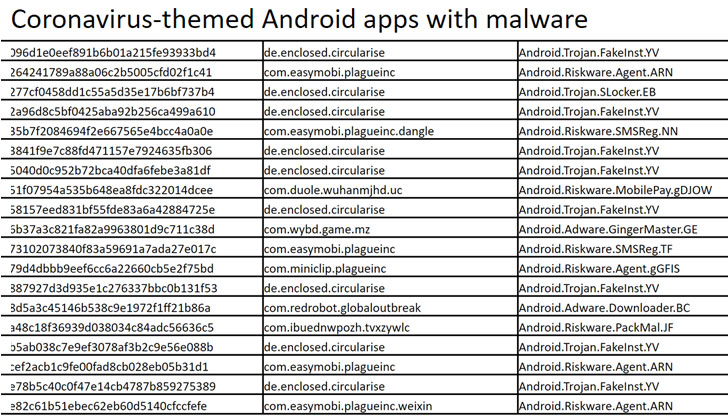
“As of January 1, 2020, we found 579 applications that contain coronavirus-related keywords in their manifest (package name, activities, receivers, etc.),” the researchers observed.
“This means that a major component of the application was named in a way – or the application contains strings – that relates it to the recent outbreak. Out of the total, 560 are clean, 9 are Trojans, and 10 are Riskware.”
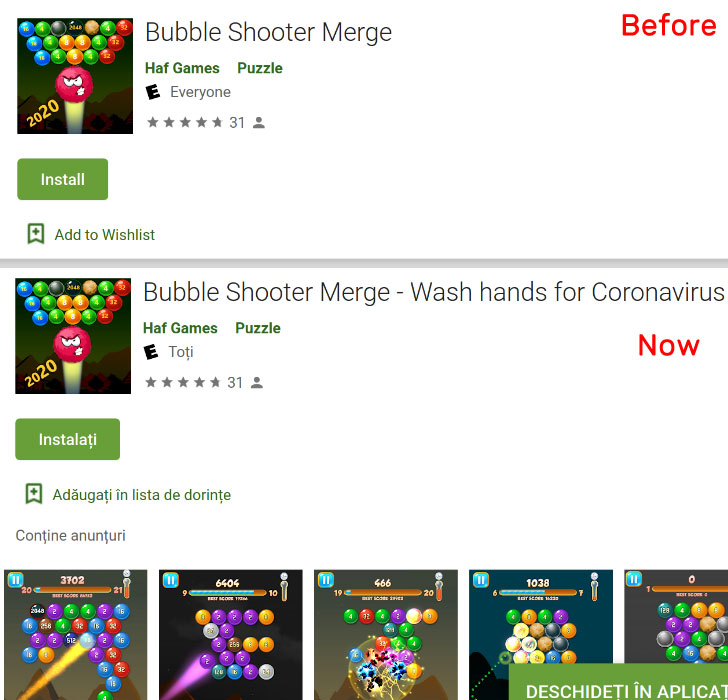
What’s more, some apps such as Bubble Shooter Merge and Galaxy Shooter – Falcon Squad have even changed their name and description to ride on the coronavirus pandemic by including keywords that ensure their apps rank higher when people search for coronavirus in the Google Play store.
This is despite Google’s strict policy against capitalizing on sensitive events and its adjustments to Google Play search results to intentionally filter out potentially malicious apps when searching for keywords like “corona” or “coronavirus.”
COVID-19 Themed Attacks Galore
From cyberattacks to phishing scams, from extortion emails to malicious websites, a long list of digital threats have leveraged on the coronavirus outbreak in recent weeks. It’s amply clear that these attacks exploit coronavirus fears and people’s hunger for information about the outbreak.
- Router Hacking — A recently discovered hack targeted home and small-office routers to redirect users to malicious sites that pose as COVID-19 informational resources in an attempt to install “Oski” malware that steals passwords and cryptocurrency credentials.
- Email Scams and Phishing — Spam emails related to the health concern have taken up close to 2.5 percent of total spam volume, indicating how email scams tied to the pandemic have steadily increased just in the month of March. What’s more, at least 42,578 “covid” or “corona” domain names have been newly registered since the start of the month, with over 2,500 new domains registered on average every single day in the last two weeks.
- Spear Phishing Attacks — Attackers have been found actively abusing the names and logos of many companies and organizations in extortion and phishing campaigns, including the World Health Organization (WHO) and the United States Centers for Disease Control (CDC), and send specially crafted RTF documents in an attempt to hoodwink their victims into downloading information stealers, remote access trojans (RATs), credential harvesters.
- Ransomware Attacks — Cybercriminals behind the Maze ransomware attacked the IT network of Hammersmith Medicines Research (HMR), a medical facility on standby to help carry out trials of any possible coronavirus vaccine, and published personal details of thousands of former patients after the company declined to pay a ransom. The development comes after the cybercrime group made a public promise not to attack medical research organizations during the coronavirus pandemic.
- Fake Apps — There has been a rise in scam campaigns and rogue apps that purport to sell coronavirus cures or face masks, or ask for investments in fraudulent companies that claimed to be developing vaccines, or urge users to make donations for fake charities.
- Banking Malware and Payment Card Hacking — The operators of Ginp banking Trojan began using information about people infected with coronavirus as a bait to lure Android users in Spain into giving away credit card data.
How to Protect Yourself
All this spate of attacks have led to the US Cyber-security and Infrastructure Security Agency (CISA) to issue warnings about the rise of Coronavirus-themed scams, and the World Health Organization (WHO) to release warnings of phishing scams impersonating their organization.
To safeguard from such threats, it’s always recommended that users install apps only from legitimate marketplaces, seek information only from official sources, and be wary of any emails attempting to get recipients to open attachments or click links.
The FBI has also issued an advisory, urging users to watch out for fake CDC emails and phishing emails asking recipients to verify their personal information —
“Scammers are leveraging the COVID-19 pandemic to steal your money, your personal information, or both. Don’t let them. Protect yourself and do your research before clicking on links purporting to provide information on the virus; donating to a charity online or through social media; contributing to a crowdfunding campaign, purchasing products online; or giving up your personal information in order to receive money or other benefits.”
Article Provided By: The Hacker News
![]()
If you would like liquidvideotechnologies.com to discuss developing your Home SecuritySystem, Networking, Access Control, Fire, IT consultant or PCI Compliance, please do not hesitate to call us at 864-859-9848 or you can email us at deveren@liquidvideotechnologies.com.


Recent Comments